April 2025 zkSync Exploit: Timeline, Impact, and Security Lessons

Introduction
In April 2025, a security breach allowed an attacker to illicitly mint 111 million new ZK tokens (~$5 million). The exploit leveraged a compromised admin key on the zkSync platform’s airdrop contracts. While the core zkSync protocol and user funds remained secure, the incident shook market confidence and underscored the importance of robust security practices in crypto projects.
In mid-April 2025, Ethereum layer-2 network zkSync suffered a notable security incident. An attacker gained control of an administrative account tied to zkSync’s token distribution (airdrop) contracts, using it to mint approximately 111 million unclaimed ZK tokens (worth about $5 million). This event – commonly referred to as the April 2025 zkSync exploit – did not stem from a flaw in zkSync’s code, but rather from a compromised admin key. In this article, we break down the timeline of the exploit, its immediate aftermath, and the broader implications for crypto security.
Timeline of the Exploit
On April 15, 2025, the zkSync team announced that one of their admin accounts had been compromised, leading to an unauthorized minting of tokens. Blockchain security researchers first spotted unusual activity, as the attacker invoked a function called sweepUnclaimed() in zkSync’s airdrop smart contracts. This function is intended to “sweep” up unclaimed tokens from the ecosystem’s airdrop – essentially gathering leftover tokens that eligible users hadn’t claimed. By calling this function through the compromised admin account, the attacker minted ~111,000,000 ZK tokens into their own address. These tokens represented roughly 0.45% of ZK’s total supply, effectively diluting the token supply overnight.
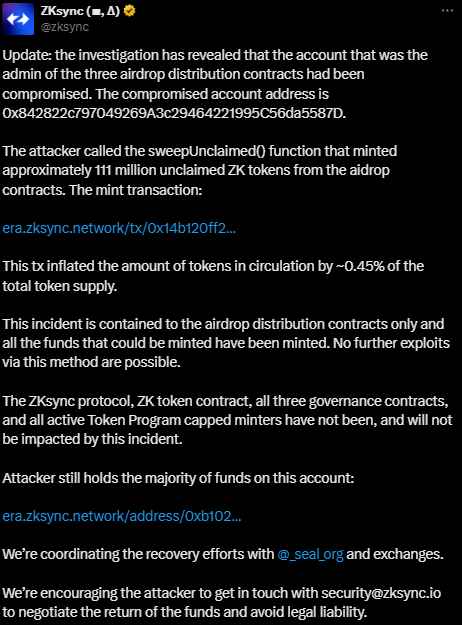
Once the breach was discovered, zkSync’s team moved quickly to identify the attacker’s on-chain footprint. They pinpointed the wallet address used by the perpetrator and noted that the attacker had begun transferring assets. On-chain data showed that the malicious account not only held the newly minted ZK tokens, but had also swapped a portion of them for other assets – even moving about 1,000 ETH to Ethereum’s mainnet shortly after. This suggested the attacker was attempting to extract and possibly launder the gains across different chains. By the time of public disclosure, the bulk of the illicitly obtained tokens remained under the attacker’s control.
Impact and Immediate Response
Despite the large number of tokens minted, zkSync’s core systems remained uncompromised. The team quickly assured users that the breach was contained to the airdrop contracts and did not affect the main network or user wallets. “All user funds are safe and have never been at risk,” the official announcement stated. In other words, the incident did not involve draining anyone’s existing balance, but rather creating new tokens from unclaimed reserves. Moreover, zkSync confirmed that all tokens that could be minted via this loophole had now been minted, and no further exploits via the sweepUnclaimed() function were possible.
In response to the attack, zkSync immediately began coordinating recovery efforts. The project worked with the crypto incident response group SEAL 911 (Security Alliance) and exchanges to track the stolen funds and prevent the attacker from cashing out. The compromised admin keys were invalidated to stop any other unauthorized actions. Notably, zkSync’s co-founder Alex Gluchowski emphasized that no flaw in the code was found – the breach resulted from an “operator key” compromise rather than a protocol bug.
The team also made a public appeal to the attacker, urging them to contact zkSync officials to negotiate a return of the funds and avoid legal consequences. This approach, increasingly common in crypto hacks, essentially offers the hacker a chance to act as a “white hat” (ethical hacker) and give back the assets, potentially in exchange for a bounty or leniency. As of the incident’s immediate aftermath, no agreement had been reached, but the outreach signaled zkSync’s intent to pursue a peaceful resolution if possible.
Market and Community Reaction
News of the exploit had a swift effect on the market price of the ZK token. Within hours of the announcement, ZK’s price plunged by over 15%, hitting an all-time low of around $0.04 on April 15. This sharp drop (roughly a $0.008 decline from the previous day’s price) reflected investors’ shaken confidence upon learning that an admin account had been breached. However, after the initial panic, the market began to stabilize. By later that day, ZK had bounced back to approximately $0.047, recovering some losses as users digested the fact that the core protocol was unaffected. Overall, the token ended up down about 7% over a 24-hour span following the hack.
ZK token’s price chart on the morning of April 15, 2025. The red line shows a sudden drop around 6:30 AM (PT) when the breach became public, followed by a partial recovery after 7:00 AM. The swift plunge to roughly $0.04 demonstrates the market’s reaction to the news, before stabilizing as more details emerged.
The community reaction to the zkSync exploit was mixed. On one hand, many users expressed relief that no one’s personal wallet was hacked and that zkSync responded quickly. On the other hand, the incident raised concerns about the project’s decentralization and security practices. Critics on social media questioned why a single admin account had the power to mint such a large number of tokens in the first place. Some even speculated about the possibility of an insider involvement, though these accusations were based on suspicion rather than evidence. The zkSync team’s transparency – providing updates, the attacker’s wallet address, and clarifying the scope of impact – was generally seen as a positive response in crisis management. Nonetheless, community members called for more robust safeguards to prevent anything similar from happening again.
Broader Security Implications and Lessons
The April 2025 zkSync exploit highlights several important lessons for the crypto industry. Firstly, it underscores the risk of admin keys in blockchain projects. In this case, the attacker didn’t find a software bug in the smart contracts; instead, they compromised a privileged key controlling those contracts. This is a stark reminder that even a well-audited codebase can be undermined if an administrator’s credentials are stolen or misused. Projects should minimize single points of failure – for example, using multi-signature (multi-sig) wallets for administrative functions, so that no single key compromise can lead to disaster.
Secondly, the exploit demonstrates the need for careful smart contract design and access control. Functions like sweepUnclaimed() serve legitimate purposes (allowing developers to reclaim unused tokens), but they also introduce centralization of power. One mitigation could be implementing time locks or multi-party approval for such sensitive functions, or automatically burning unclaimed tokens after a deadline instead of keeping them accessible. Had the unclaimed tokens been truly inaccessible to any single key, the attacker would have had nothing to exploit.
Regular security audits and ongoing code reviews are essential, but they must extend beyond just checking for bugs – they should also evaluate how administrative privileges are managed. In the zkSync case, the contracts worked as intended, yet the overall security architecture (the admin key management) had a weakness. External auditors and security experts often flag excessive admin privileges or lack of multi-sig as a potential risk in decentralized finance (DeFi) systems; this incident validates those warnings.
Another broader implication is the value of community and industry collaboration when hacks occur. zkSync’s coordination with the SEAL 911 alliance and exchanges shows that the crypto community can come together rapidly to respond to incidents. Exchanges can blacklist the attacker’s addresses, and security teams can share information to help track and possibly freeze assets. This kind of collective defense is becoming more common as the industry recognizes that “fighting alone” against exploits is less effective.
Finally, the incident fits into a larger pattern of crypto projects seeking unconventional solutions after a breach. In some recent cases, teams have offered bounties to hackers for returning funds – a strategy born out of necessity. For example, around the same time as the zkSync exploit, the DeFi exchange KiloEx faced a separate $7.5 million hack and publicly offered the hacker a 10% “white hat” bounty (approximately $750,000) to encourage the return of the remaining funds. KiloEx’s ultimatum to the thief – return 90% or face legal action – exemplifies how projects are willing to negotiate to recover assets. While the zkSync team did not immediately propose a specific bounty, their invitation for dialogue with their attacker follows the same logic of preferring a negotiated resolution to a protracted chase.
The key takeaway for crypto developers and communities is that preventative measures are far better than reactive ones. Strengthening access controls, practicing good operational security (for example, secure storage of keys and avoiding phishing), and planning for incident response can make all the difference. Likewise, users and investors in crypto projects are now more aware of the questions to ask: Does the project have admin keys that could be abused? What safeguards and fail-safes are in place? Transparency about these aspects can build trust long before any incident occurs.
Conclusion
The zkSync exploit of April 2025 was a wake-up call that even advanced blockchain systems can be vulnerable through their administrative backdoors. In this case, an attacker managed to create $5 million in tokens out of thin air, yet the quick action by the team ensured that the damage was limited to token dilution and market turbulence, not loss of user deposits. The event had a measurable but temporary effect on the ZK token’s value and prompted important discussions about security.
For zkSync, restoring confidence will involve reinforcing their key management and perhaps adjusting how such a large cache of tokens can be controlled. For the wider crypto community, this episode reinforces the importance of decentralizing control and thoroughly vetting not just code, but also the people and processes that have power over that code. As blockchain projects continue to evolve, balancing functionality (like reclaiming unclaimed tokens) with safety will remain a crucial design challenge.
Ultimately, the incident may serve as a valuable lesson that drives improvements in the industry. By learning from events like the zkSync admin key breach, developers and organizations can implement better safeguards—ensuring that the only things getting “swept” in future airdrops are genuine leftovers, and not the security rug from under an entire community.


Comments ()