Cross‑Chain Interoperability: Why Bridges Remain Web3’s Weakest Link

In Web3’s multi chain future, interoperability is critical. Users need to move assets, data, and state across chains, but cross-chain bridges, while essential, have been the single largest source of protocol exploits in crypto history. Over $2.5 billion in assets has been stolen from bridge hacks since 2021, per Chainalysis and CertiK. Despite technological progress, 2025 still sees bridges struggling with core challenges: fragmented trust models, centralization risks, and complex attack surfaces.
Bridge Architecture: Strengths and Flaws
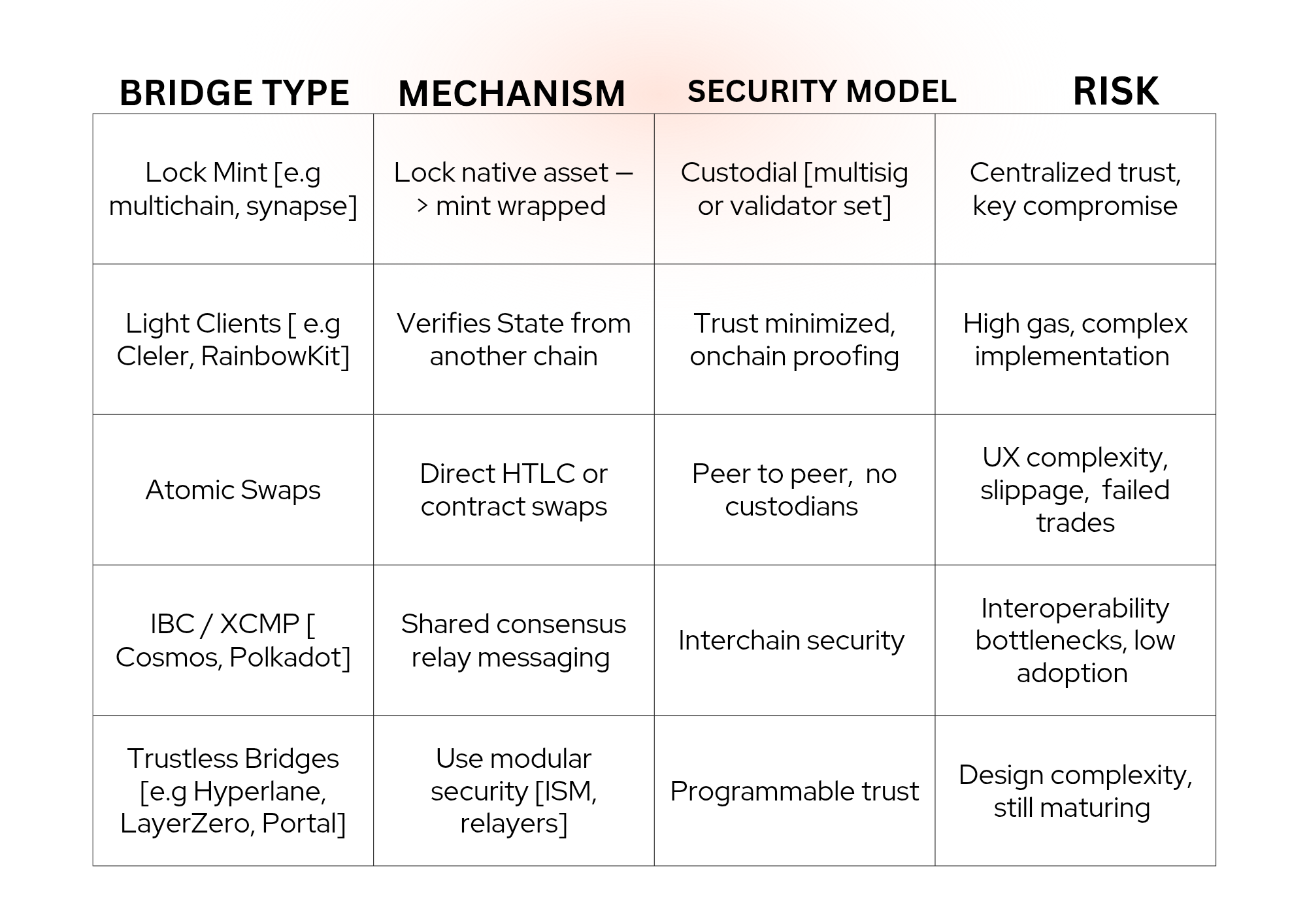
Key Takeaway: Most bridges rely on some form of off chain trust assumption, either in relayers, validators, or multisigs. These assumptions create attack surfaces.
Common Bridge Vulnerabilities
Bridges are especially vulnerable due to the complexity of syncing two or more distributed systems with different rulesets. Common exploits include: ■ Access Control Flaws: Improper permission setups allow attackers to mint or release assets. ■ Replay Attacks: Transaction replays across forks or duplicate chains. ■ Oracle Manipulation: Faulty price feeds or state updates trick the bridge into invalid asset releases. ■ Meaningful Mismatch: Assumptions made by one chain don't apply to the other, leading to logic errors. ■ Bridge Contract Bugs: Improper handling of proof verification or locking logic. ■ One infamous case: the Wormhole exploit (2022) led to a $325M loss due to a signature verification bypass.
Security Enhancements & Emerging Standards
1. Formal Verification + Static Analysis: Projects like SmartAxe, VeriX, and BridgeGuard apply formal logic tools to analyze bridge contracts for invariants and edge cases. 2. Interchain Messaging Protocols (XCMP, IBC): Shared security models help, but interoperability is gated by limited compatibility and validator coordination overhead. 3. Modular Security (Hyperlane, LayerZero, Portal): Allow chains to define their own Interchain Security Modules (ISMs). Trust assumptions are customizable, leading to programmable and layered security. 4. Onchain Verification (Succinct ZK bridges): Using zkSNARKs for cross-chain state proofs (e.g zkIBC) avoids relayer trust but is still cost intensive and early stage.
What’s the Real Barrier?
Even with advanced bridge protocols, the ecosystem faces: ● UX friction: Users often don’t understand trust assumptions or fees. ● Developer burden: Supporting each new chain requires heavy integration work. ● Economic incentives misaligned: Many bridges are initiated without robust validator or relayer incentive mechanisms.
Summary
Cross-chain bridges are mission critical to a modular future, but they remain structurally fragile in 2025: • Security is fragmented across competing models. • Composability is limited by protocol mismatch and validator coordination. • Users remain exposed to loss due to core architecture flaws. Until trustless, standardized solutions like ZK light clients or robust modular messaging systems become widespread, bridges remain the weakest link in Web3.
🔗 Links to Explore More
Bridge Security & Exploit Data https://www.chainalysis.com/blog/bridge-hacks-2023-crypto-crime/ https://www.certik.com/resources/blog/bridge-exploits-security-risks Cross-Chain Architecture Deep Dives https://vitalik.eth.limo/general/2022/01/07/cross.html https://www.delphidigital.io/reports/interoperability-in-crypto/ https://l2beat.com/bridges/ Trustless & Modular Protocols https://docs.hyperlane.xyz/ https://docs.layerzero.network/ https://portaldefi.notion.site/Portal-Whitepaper-e7c379ad3c254cb5b0713a4d5076e6f1 ZK & Formal Verification Approaches https://github.com/informalsystems/ibc-rs/tree/main/integrations/zk https://www.smartaxe.ai/ https://veridise.com/
Check mitosis and use expenditure bridge free
Mitosis Expedition (LP Campaign): https://expedition.mitosis.org/
Mitosis Discord: https://discord.gg/mitosis?ref=university.mitosis.org


Comments ()