Drosera: Codifying Security as Decentralized Automation in DeFi
Introduction
Drosera emerges from the DeFi world as a developer-centric, decentralized protocol designed to automate real-time security. Far from traditional reactive measures like audits or multisigs, Drosera enables protocols to define Traps, Solidity-based programmable tripwires that detect and respond to anomalous on-chain activity.
Its an architecture that unites on-chain configuration with off-chain monitoring powered by decentralized Operators, delivering both trustlessness and automation.
In a domain where speed matters and threats evolve, Drosera empowers protocols to encode their defense logic directly into their infrastructure, making security proactive, not an afterthought.
Core Components Explored
→Traps
At the heart of Drosera are Traps, Solidity contracts acting as customizable detectors and responders.
- Off-chain layer: The Trap logic continuously collects block-level state such as asset prices, collateral ratios, and volumes, and analyzes it via functions like
shouldRespond(). This approach provides contextual intelligence while keeping gas costs low. - On-chain layer (Trap Config): A compact smart contract holds the hash of the off-chain code and points to the on-chain callback function such as
pause()orreact(address). This modular pairing allows protocols to define responses securely and transparently.
Together, the dual-layer Trap system offers powerful flexibility. Complex analysis can happen off-chain while execution remains auditable and trustless on chain.
→Operators
Operators form Drosera’s decentralized defenders.
- Role: They run the Operator Client, via Docker or binaries, and opt into specific Traps. Once opted in, they monitor block activity off-chain, evaluate triggers, and upon consensus, execute the on-chain response.
- Decentralization and Incentives: Anyone can become an Operator including individuals, security firms, or DAOs. Incentives take the form of Hydration Streams, which continuously fund Traps, and direct rewards for valid incident responses. Slashing mechanisms deter malicious behavior.
- Consensus: Multiple Operators must independently validate the trigger, often via a two-thirds consensus, before the response is broadcast. This enhances reliability.
→Seed Nodes
Seed Nodes underpin the integrity and resilience of the network.
High Architecture
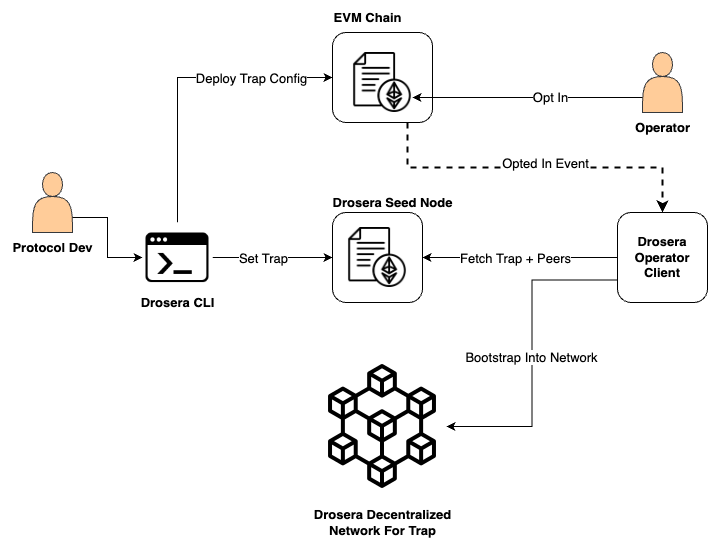
- Function: They host Trap bytecode and facilitate Operator onboarding. When an Operator opts into a Trap, the Seed Node delivers the associated bytecode securely.
- Trust Infrastructure: Only vetted, trusted Seed Nodes, listed in the documentation, should be used to prevent tampering.
How Drosera Operates Architecturally
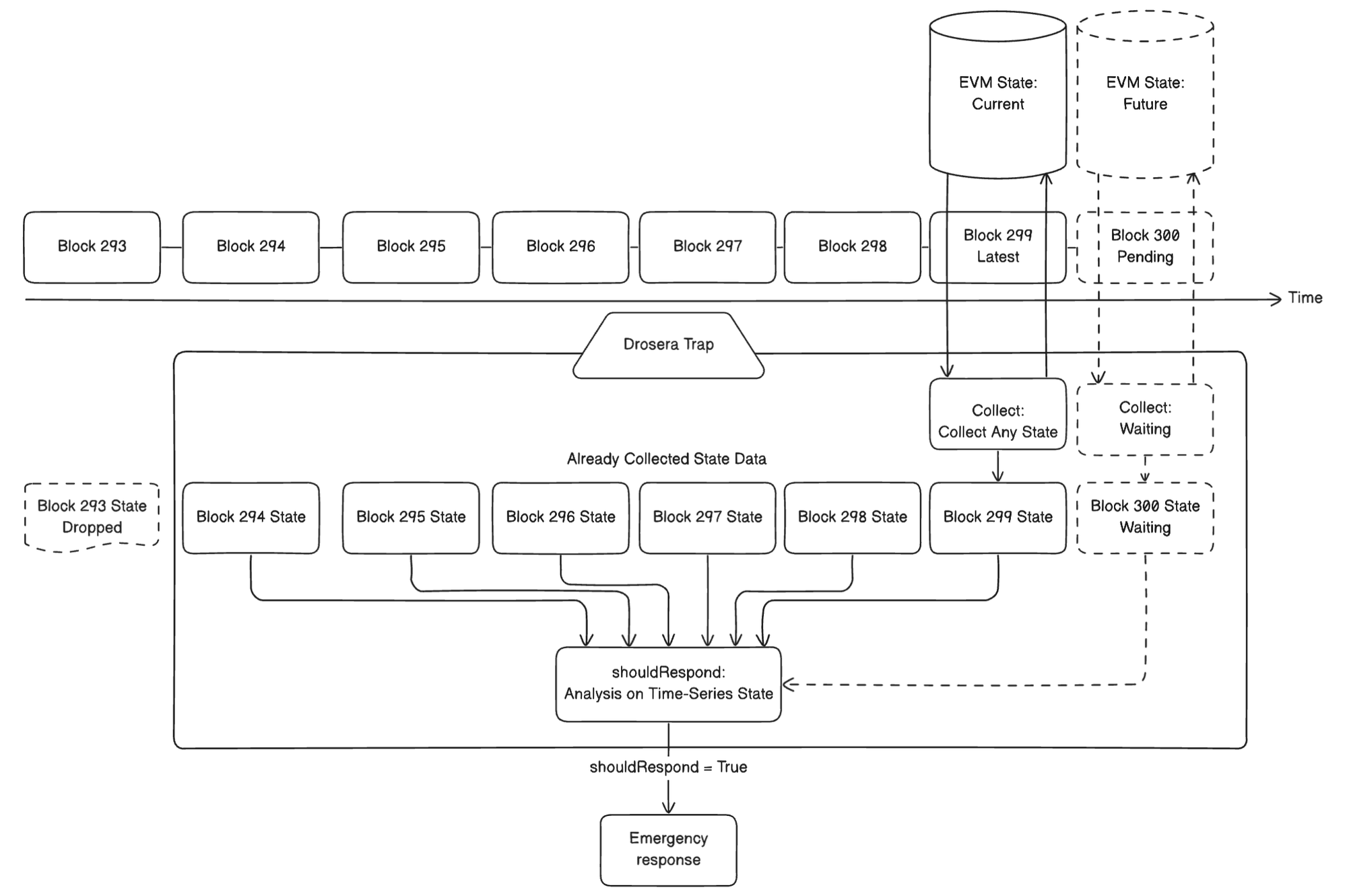
→Workflow
- A developer identifies critical protocol behavior such as flash-loan exploits or collateral ratio drops, and writes a Trap that collects data and responds in Solidity.
- The Trap Config is deployed, pairing the off-chain logic with its on-chain callback.
- Operators register and opt into the Trap, receiving the bytecode via Seed Nodes.
- In each block, Operators run the Trap logic off-chain. If the condition is met and consensus is achieved, one Operator submits the on-chain transaction.
- Hydration Streams feed the Trap’s reward pool, ensuring Operators remain motivated to act.
→Unique Innovations
- Hidden Traps: Detection logic can be obscured, making exploits riskier for attackers.
- Bloom Boost: Drosera can add ETH to prioritize its emergency transactions in the mempool, minimizing latency.
- Near-Immediacy: Some implementations have demonstrated response times as low as two to three seconds post-alert, with automatic pausing to thwart flash attacks.
- Composable SDKs: Drosera integrates with developer tools like Foundry, RiscZero proofs, and LibP2P for off-chain networking.
Real-World Use Cases and Ecosystem
—Use Cases Across DeFi
Drosera's flexibility makes it relevant across various DeFi verticals:
- Lending: Automate alerts or partial liquidations when collateral dips below thresholds.
- DEXs and Oracles: Detect rapid changes in volume or pricing, flag manipulation.
- Bridges and L2s: Monitor for failed fraud proofs or paused bridges and trigger alerts.
- Staking Protocols: Guard against reward draining or bugs in locking logic.
- Treasury Management and Governance: Auto-pause suspicious withdrawals or flag strange multisig or governance actions.
- Parametric Insurance and Cross-Protocol: Use Traps to automate claims or monitor inter-protocol dependencies.
→Ecosystem Growth and Adoption
Drosera raised 4.75 million USD in early 2025, backed by Greenfield Capital and others, to advance mainnet readiness and expand its tooling.
Notable testnet deployments include Ion Protocol, Gravita, EsterFi, and others. The roadmap projects zk-proof enhancements, multi-chain expansion, and governance features.
Media coverage frames Drosera as Ethereum’s immune system, a paradigm shift toward programmable, decentralized DeFi security.
Value Proposition and Strategic Advantages
Developer-Centric Security
- Proactive, codified defense: Traps allow precise and programmable security logic tailored to protocols.
- Lower gas costs: Off-chain monitoring reduces unnecessary on-chain activity.
- Composable integration: Build in Traps using familiar Solidity tooling and reliable SDKs.
Decentralized and Incentive-Aligned
- Permissionless defenders: Anyone can operate, fostering a distributed security mesh.
- Aligned incentives: Hydration Streams and reward pools tie protocol security to Operator action.
- Resilience through consensus: Multi-operator validation minimizes false positives or single-point failures.
Responsive and Obfuscation-Based Defense
- Real-time countermeasures: From pauses to redirections, responses can happen in under a block.
- Security through secrecy: Hidden Traps reduce attacker clarity, increasing exploit risk.
- Execution priority: Bloom Boost ensures defense transactions are mined promptly.
How to Start Building with Drosera
For developers:
- Define threats: Identify attack surfaces like re-entrancy, oracle manipulation, or governance exploits.
- Write Traps: Use Trapper-friendly SDKs to code
collect()andshouldRespond()ordetect()andrespond()functions. - Deploy Trap Config: Link off-chain logic to on-chain response actions securely.
- Fund the Trap: Initiate Hydration Streams to ensure continuity.
- Test and iterate: Use testnet faucet and dry-run features to simulate attack vectors.
Operators interested in participating should:
- Run the Operator Client, register an Ethereum account, and opt into Traps.
- Maintain uptime and responsiveness, critical for earning Hydration-based rewards.
Conclusion
Drosera redefines security in DeFi by weaving it into the code itself, turning detection and response into a programmable, trustless process. With developer-first SDKs, incentivized Operators, and resilient architecture, it positions security as composable infrastructure rather than an afterthought.
As the DeFi landscape grows, Drosera’s model, like an immune system, can scale defense organically and intelligently. Whether you are a protocol architect, security researcher, or community builder, Drosera invites you to embed defense into your platform’s DNA. The future of DeFi security can be coded, automated, and decentralized, one Trap at a time.
TLDR; Summary Table
| Component | Role |
|---|---|
| Traps | Programmable detection and response logic (off-chain and on-chain) |
| Operators | Decentralized defenders running monitoring clients and executing responses |
| Seed Nodes | Infrastructure for Trap distribution and Operator onboarding |
| Hydration Streams | Continuous funding mechanism to incentivize Operators |
| Unique Edge | Hidden logic, Bloom Boost, fast consensus, scalability |



Comments ()