HOW MITOSIS KEEPS YOUR LIQUIDITY SAFE
In DeFi, a single bad click can cost you everything. Imagine loosing your whole liquidity after accidentally approving a malicious contract. Painful, but sadly common.
It’s exactly this kind of risk that Mitosis architecture was built to neutralize. Not just by telling users “be careful,” but by fundamentally designing vaults that can’t be drained by outside approvals.
Let’s Break Down Why, And How It Really Works
The Vault Isn’t Just a Safe; It’s Smart Custody
When you deposit assets into Mitosis, those tokens don’t stay in your wallet, exposed to random approvals. Instead, they’re moved into dedicated Vault contracts; each deployed per asset, per chain. These Vaults do two things:
1. Lock the actual tokens so they can’t be pulled out directly
2. Talk to the Mitosis L1 to mint you a matching Hub Asset (like a Vanilla Asset), representing your position
The Hub Asset lives on Mitosis’ own L1 (built on Cosmos, but EVM-compatible). From the Litepaper:
“Mitosis Vaults are smart contracts…facilitating secure asset custody… underlying tokens remain safely stored in the Vault.”
The Vault contracts are completely isolated from external contracts. No random dApp or malicious contract can touch them, they only listen to the Asset Manager, which is part of the protocol’s trusted bridge & minting system.
So right from deposit, your real assets are locked away in a controlled box, and what you trade or use are the Vault tokens that mirror your ownership
Withdrawals Need Real, Signed Redemption — Not Just Transfer
Okay, but how do you get your money back?
Even here, Mitosis stops malicious approvals from draining you.
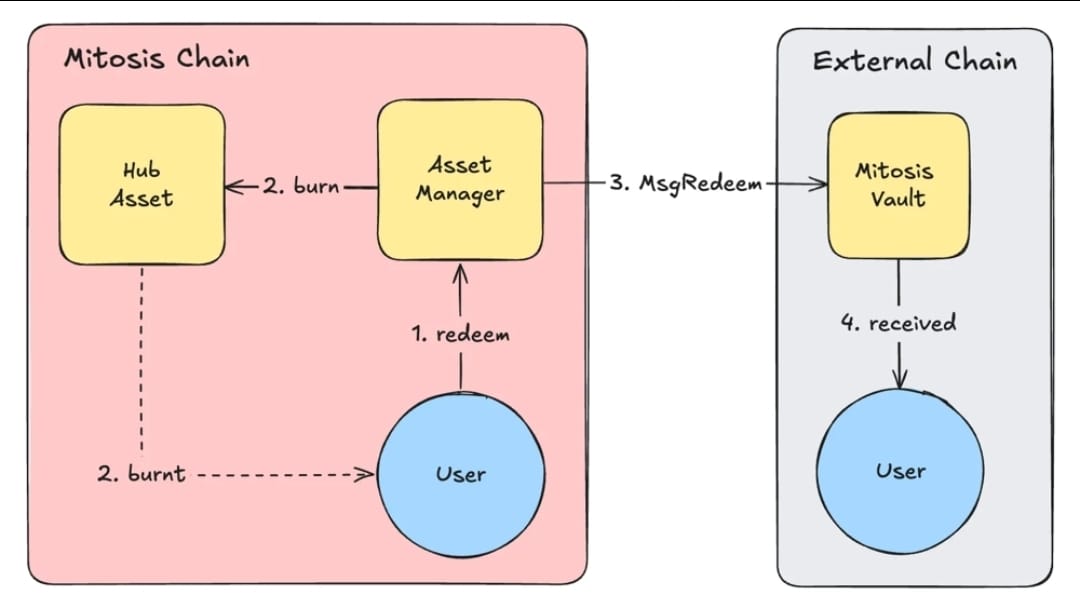
Here’s the flow: You burn your Hub Asset on the Mitosis L1
That sends a redeem message to the original Vault
The Vault then releases the underlying tokens back to your wallet.
Notice: You have to initiate this burn. Only the Asset Manager (trusted protocol contract) can send the redeem message. The Vault won’t hand out funds unless it sees a valid burn-and-redeem flow.
So even if you accidentally approve a shady contract to move your Hub Assets around, it still can’t force the Vault to cough up your real funds. The burn must come from a legitimate user-signed transaction → anything else is ignored.
Why This Actually Matters (Beyond Buzzwords)
This isn’t just marketing.
In normal DeFi:
You LP, get an LP token, approve a random farming contract
That contract can call transferFrom and move your LP token → then claim your share of the pool → your funds vanish In Mitosis: You deposit once
The Vault locks funds; you get a Hub Asset
Even if a malicious contract gets approval to transfer that Hub Asset, it can’t redeem the real underlying assets from the Vault unless it follows protocol logic
And that logic can’t be triggered without your explicit burn and cross-chain message In effect: Approvals don’t equal withdrawals
Vaults only unlock funds for the real depositor following the proper protocol steps That’s why the Litepaper calls it:
“Liquidity is not a product. It’s an operating system.” Vault tokens aren't just passive receipts; they’re living records tied to the protocol's accounting and security logic.
Extra Layers: Governance & Strategy Controls
The design goes further.
For long-term Ecosystem Owned Liquidity (EOL) vaults: Where funds get redeployed isn’t automatic
Strategies must pass on-chain votes
Governance uses TWAB (Time Weighted Average Balance) → LPs who stay longer get more say So even if someone tried to rush through a malicious strategy, short-term whales wouldn’t have the votes to do it.
Plus:
The Vault contracts and cross-chain logic are audited
Assets are kept in isolated contracts per vault and per asset All of this stacks together: architectural separation + governance + vault logic.
Real-World Example: Why This Protects You
Imagine you hold USDC, deposit into a Matrix vault:
The Vault mints you maUSDC
Your USDC is now safe inside the Vault You see a random farm on Telegram: “Approve us to spend your maUSDC for 500% APY!” If you approve them?
All they get is permission to transfer your maUSDC; they still can’t redeem the actual USDC sitting in the Vault. Only your signed burn message + Asset Manager + vault logic can do that.
📚 Sources Mitosis Litepaper


Comments ()