Laying the Foundation: 'The One-Time Setup' for Nexus zkVM Architecture

The Nexus Vision: A Foundation for Verifiable Computing
The Nexus zkVM is a groundbreaking system designed to make verifiable computation scalable, practical, and trustless, as explored in our earlier articles. In "Verifiable Computation at Scale: How the Nexus zkVM Redefines What’s Possible with Zero-Knowledge Proofs," we introduced the zkVM as a universal prover, capable of generating zero-knowledge proofs for any program, with a five-stage pipeline optimized for massive computations. "The Nexus Virtual Machine (NVM): A Finely Tuned Engine for Verifiable Computation" detailed the NVM, a minimal, prover-efficient CPU architecture tailored for zero-knowledge proofs, enhanced by modular co-processors. Finally, "Scaling Verifiable Computation: The Nexus Network, A Verifiable Supercomputer" showcased the Nexus Network, a distributed infrastructure that scales proof generation across global provers, transforming the zkVM into a verifiable supercomputer. The One-Time Setup, the first stage of the zkVM’s pipeline, lays the critical foundation for this architecture, configuring the NVM and cryptographic parameters to enable secure, efficient, and scalable proofs.
Introduction: Laying the Foundation for Proofs
Before the Nexus zkVM can work its zero-knowledge magic, proving a program's execution with privacy and efficiency, it needs a solid foundation. The One-Time Setup is the critical first stage in this process, performed only once for a given virtual machine configuration. This phase defines the computational environment and cryptographic rules, enabling all subsequent program executions and proofs. Here’s how it works, why it matters, and how it sets the stage for the Nexus zkVM’s verifiable computations.
What Happens in the One-Time Setup?
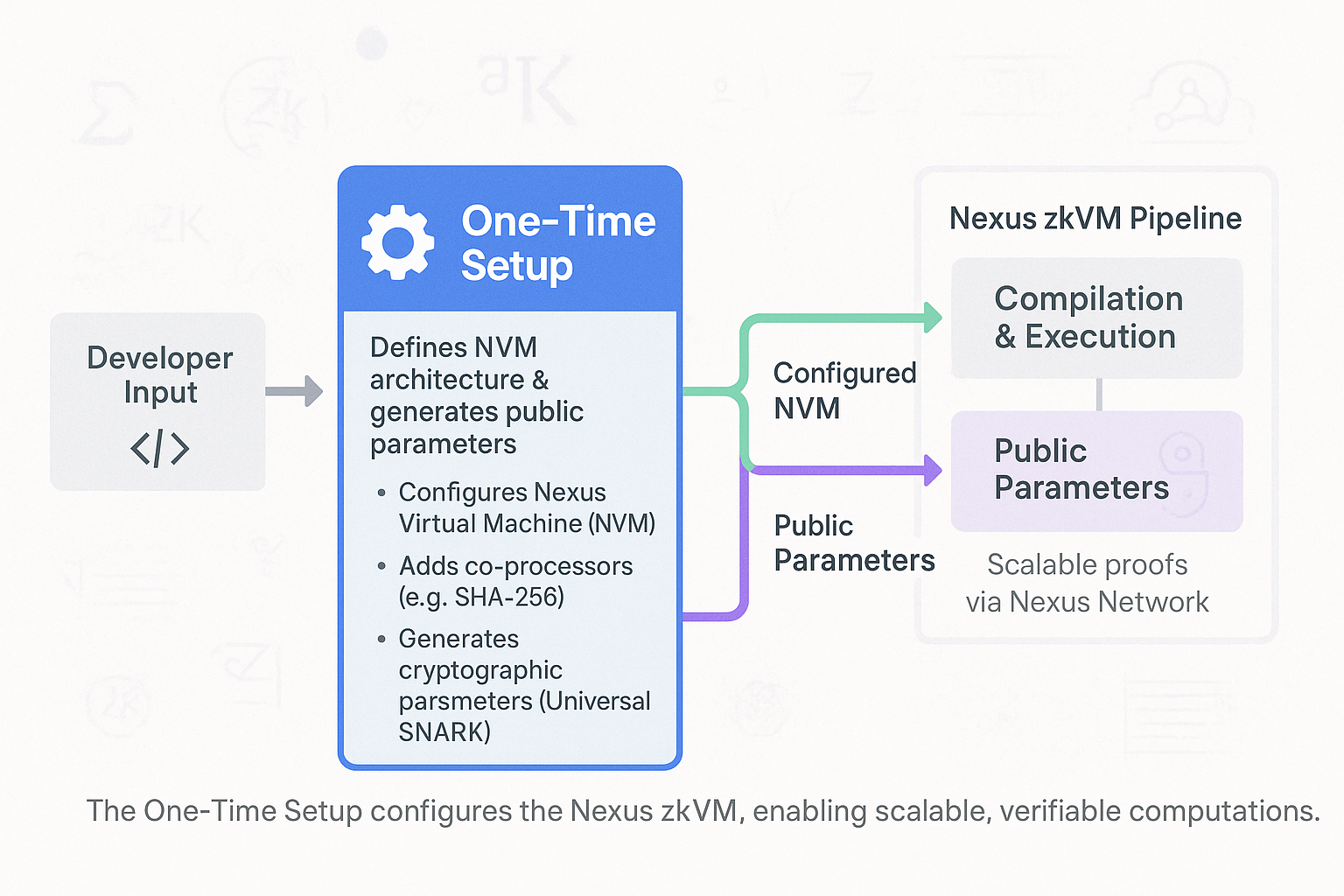
The One-Time Setup establishes the groundwork for the Nexus zkVM by configuring the virtual machine and generating the cryptographic keys needed for zero-knowledge proofs. Unlike later stages, which focus on specific programs, this phase is about preparing the system itself. It involves three key components:
- Defining the Machine Architecture: The setup begins by specifying the Nexus Virtual Machine (NVM) instruction set—a streamlined, 32-bit CPU architecture with about 40 instructions, optimized for prover efficiency, as detailed in our Nexus Virtual Machine article. This minimal design ensures computations are compact and proof generation is fast.
- Incorporating Co-Processors: Developers can extend the NVM by adding co-processors—specialized, pre-proven circuits for computationally intensive tasks, such as SHA-256 hashing or signature verification. These modular components, a hallmark of the NVM’s extensibility, enhance the zkVM’s flexibility for diverse applications.
- Generating Public Parameters: The setup concludes by creating cryptographic public parameters—shared data that define the rules for generating and verifying proofs without revealing program details. Generated using the Nexus zkVM’s Universal SNARK framework with polynomial commitments, these parameters ensure the soundness and zero-knowledge properties of the system, guaranteeing that proofs are valid and private.
This one-time process ensures the zkVM is ready to compile, execute, and prove any program within the defined environment, from blockchain smart contracts to privacy-preserving machine learning models.
Why Co-Processors Matter
Co-processors are a standout feature of the Nexus zkVM, reflecting its modular design, as discussed in our Nexus Virtual Machine article. By embedding specialized operations as native instructions, co-processors reduce the computational burden of proof generation for complex tasks. For example:
- A blockchain developer might include a co-processor for SHA-256 hashing to efficiently prove smart contract executions.
- A data scientist could add matrix multiplication instructions to support privacy-preserving machine learning models.
This modularity allows developers to tailor the zkVM to specific use cases, balancing performance and functionality while preserving the NVM’s prover-efficient core, as highlighted in our Nexus architecture article.
Practical Implications: A Real-World Example
Consider a decentralized finance (DeFi) platform that needs to prove the correct execution of a smart contract while keeping sensitive transaction data private. During the One-Time Setup, the developer configures the zkVM with a co-processor for elliptic curve cryptography, optimizing proof generation for signature verification. The public parameters are generated once, enabling the platform to prove countless transactions without repeating this setup. This reusability across unlimited programs makes the Nexus zkVM highly scalable and cost-effective for developers, supporting applications from zkRollups to zkML, as explored in our Nexus architecture article.
Connecting to the Broader Workflow
The One-Time Setup is the foundation of the Nexus zkVM’s five-stage pipeline, as outlined in our Nexus architecture article. By defining the machine architecture and cryptographic parameters, this stage enables:
- Stage 2: Program Compilation—Translating programs into the configured NVM instruction set.
- Stage 3: Execution and Proof Generation—Running programs and creating verifiable proofs.
- Stage 4: Folding—Parallelizing proof generation across the Nexus Network.
- Stage 5: Compression—Producing a succinct zk-SNARK for verification.
The parameters generated in Stage 1 also enable lightweight verification, allowing verifiers to check proofs quickly and securely, a critical advantage for applications like blockchain consensus or verifiable AI, as discussed in our Nexus Network article.
Addressing Common Questions
- Is the setup computationally intensive? Yes, generating public parameters requires significant computation due to cryptographic operations like polynomial commitments. However, this one-time cost unlocks faster proof generation, reusability across many programs, and long-term efficiency for diverse applications.
- What if I need new co-processors? Adding or modifying co-processors requires a new setup, as the architecture and parameters must be updated. This is rare once the VM is configured for a specific application.
- How does this differ from other zkVMs? The Nexus zkVM’s Universal SNARK, co-processor modularity, and distributed proving via the Nexus Network provide unmatched flexibility and scalability, distinguishing it from less customizable systems like RISC Zero or Cairo, as compared in our Nexus architecture article.
One-Time Setup at a Glance
Component | Description |
|---|---|
Define Architecture | Select the Nexus Virtual Machine’s 32-bit instruction set, optimized for proofs. |
Add Co-Processors | Include specialized circuits (e.g., SHA-256, matrix operations) for efficiency. |
Generate Parameters | Create cryptographic keys using Universal SNARK for proof generation/verification. |
Conclusion
The One-Time Setup is the unsung hero of the Nexus zkVM, laying the cryptographic and computational groundwork for verifiable execution. By defining the NVM architecture, incorporating co-processors, and generating secure public parameters, this stage unlocks the zkVM’s potential for privacy, scalability, and efficiency. As the first step in the Nexus architecture’s pipeline, it enables everything from smart contract offloading to verifiable AI, setting the stage for a new era of trustless, internet-scale computation.
Similar Articles
zk‑SNARKs to zk‑STARKs: The Evolution of Zero‑Knowledge in Web3
Succinct SP1 zkVM: Democratizing Zero-Knowledge Proofs for Rust Developers
🧬 How Replacing the EVM with RISC-V Could Accelerate Mitosis’ Programmable Liquidity Vision
The Future of Web3 Security: Verifiability Without Visibility Using zkTLS and FHE
Unpacking Blockchain's Engines: A Comprehensive Look at Virtual Machines



Comments ()