Mastering Web3 Security: Essential Tips to Protect Your Crypto and Blockchain Assets

You've heard the buzz, felt the pull – the decentralized world of Web3, crypto, and blockchain beckons with the allure of independence and new possibilities. It feels like stepping into a digital frontier, vibrant and full of potential. Yet, like any frontier, it has its dangers. Without central authorities to catch you, the responsibility for protecting your digital future rests squarely on your shoulders. Scams are sophisticated, hacks are relentless, and the immutable nature of the blockchain means mistakes are often permanent. Ready to explore, but want to make sure you don't get lost in the digital wilderness? This article is your compass and your shield, packed with practical, expert strategies to help you navigate Web3 safely, secure your assets, and confidently outsmart the bad actors lurking in the shadows.
Why Web3 Security Matters More Than Ever 🌐

Web3 shifts the internet from centralized control (think Big Tech) to a decentralized model where you own your data, powered by blockchain and cryptocurrencies. Unlike Web2, where banks or companies might reverse fraudulent transactions, Web3 has no safety net—once a transaction is confirmed, it’s final. There’s no centralized authority to call for help if you’re scammed, so you need to be your own security guard. From managing private keys to dodging sophisticated attacks, staying safe is non-negotiable in this wild, decentralized west.
The Threats Lurking in Web3: Know Your Enemies 🕵️
Web3’s innovation attracts malicious actors. Here’s a rundown of the biggest dangers:
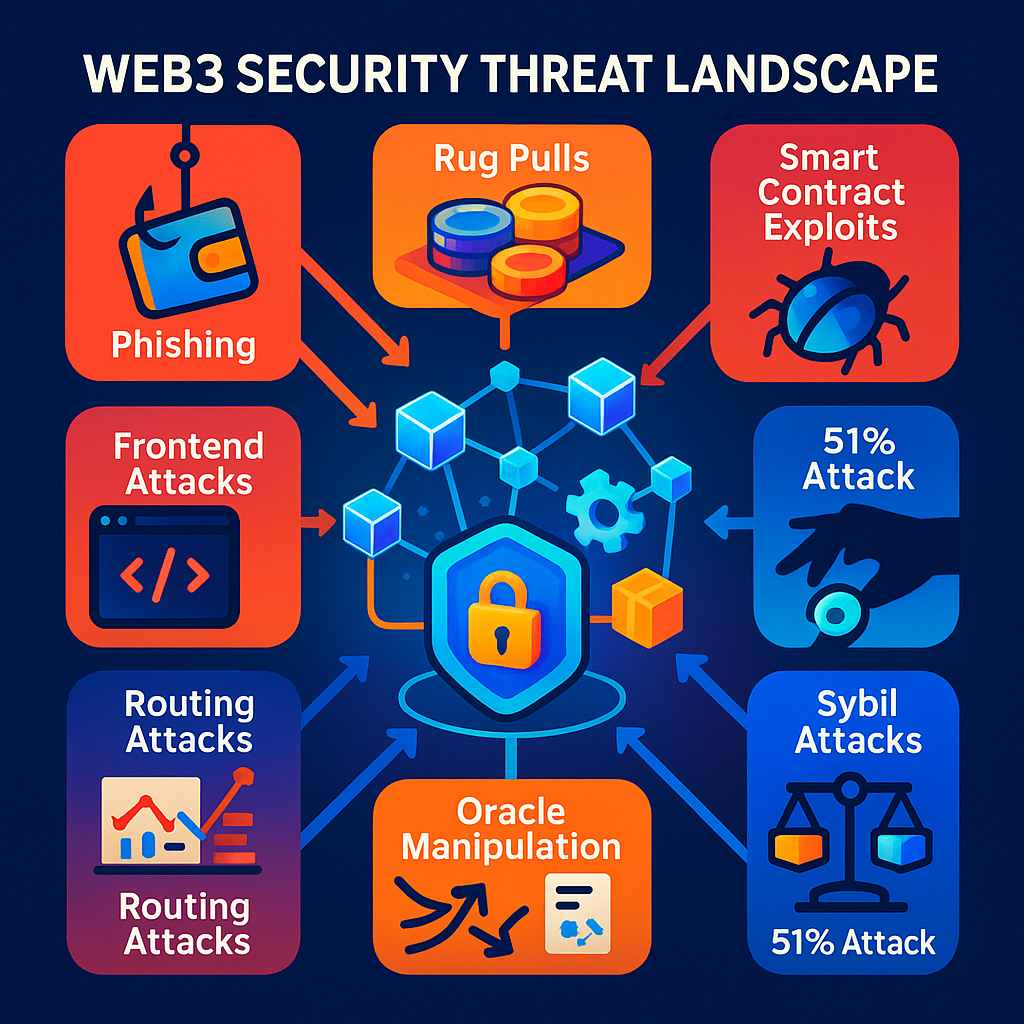
- Phishing Attacks 🎣: Scammers create fake websites or messages mimicking platforms like OpenSea, tricking users into revealing private keys or signing malicious transactions. In 2022, OpenSea users lost NFTs to fraudulent smart contracts via phishing.

Fake job offers or impersonated support accounts on social media add to the danger. .
- Rug Pulls 🤑
Common in DeFi, developers hype a project, then vanish with funds. The 2021 Squid Game Token scam saw creators disappear with $3.3 million, leaving investors with worthless tokens. Unaudited projects and anonymous teams are red flags. RugDoc is a resource for evaluating DeFi projects for rug-pull risk. - Smart Contract Exploits 🐞
Bugs like re-entrancy (e.g., the 2016 DAO hack), integer overflows, or unchecked external calls let hackers drain funds. Most contracts are immutable, so flaws are hard to patch. Immunefi tracks Web3 exploits and bounties. - Private Key Theft 🔑
If someone gets your private key—via malware, phishing, or clipboard hijacking—they own your funds. In 2024, multiple cases of clipboard swapping malware made headlines. SlowMist frequently reports on these exploits. - Consensus Attacks (51% Attacks) ⚔️
Hackers controlling over 50% of a blockchain’s power can rewrite the ledger, double-spend coins, or block transactions. Ethereum Classic faced several such attacks in 2020. - Sybil Attacks 🕸️
Attackers flood the network with fake nodes to control traffic, spy on users, or block transactions, undermining the consensus process. - Routing Attacks 🌐
Hackers intercept consensus requests or isolate nodes, disrupting transactions or ledger updates. - Oracle Manipulation 📊
Oracles feed real-world data to smart contracts. If tampered with, they can trigger faulty logic—like buying assets at a discount or causing liquidations. Chainlink combats these threats with decentralized oracles. - Cloud Vulnerabilities ☁️
Many projects rely on centralized cloud infrastructure. Misconfigured APIs or unpatched servers open the door to attackers. Regular security audits are crucial. - Access Control Exploits 🔓
Multisig wallet hacks, like those hitting Bybit and Phemex, often stem from sloppy signer protocols or poor offboarding of signers. - Frontend Attacks (XSS) 💻
Attackers inject code into dApp frontends to steal keys, redirect users, or alter contract behavior. - API Vulnerabilities 🔌
APIs power most dApps. Vulnerabilities like improper authentication can let attackers bypass controls or overload services. - Unauthorized Data Access 📂
Some breaches don’t just steal funds—they compromise sensitive user data. Always minimize what data dApps can access.
Lock Down Your Crypto: Wallet Security Tips 🔒
Your wallet is your Web3 gateway—keep it secure! Wallets are either custodial (a third party like an exchange holds your keys) or non-custodial (you control your keys), and hot (online) or cold (offline). Here’s how to stay safe:
- Custodial Wallets: Pick trusted providers with strong security (e.g., 2FA, cold storage). But if they’re hacked or go bankrupt, your funds are at risk. Be extra cautious on mobile devices—they’re more vulnerable.
- Non-Custodial Wallets: You’re in control, but also fully responsible. Back up your seed phrase offline (write it on paper or metal, store in a safe—not your phone!). Use strong passwords, enable 2FA, and consider a hardware wallet for big holdings. Update wallet software regularly, encrypt devices if storing sensitive info, and use multisig wallets for large amounts.
- Hot vs. Cold Wallets: Hot wallets (mobile apps, browser extensions) are convenient for trading but riskier due to internet exposure. Cold wallets Tools like Trezor or Ledger offer safer cold storage options. keep keys offline, ideal for long-term storage. Use both: small amounts in hot wallets, the rest in cold storage.
- Multisig Wallets: Wallets like Safe (formerly Gnosis Safe) require multiple keys to approve a transaction. Ideal for DAOs or large portfolios.
- Password & Backup Tips: Use complex, unique passwords (a password manager helps). Store seed phrase copies in separate, secure spots (e.g., fireproof safes). Metal backups resist fire and water damage. Never store digitally unless encrypted.
Safely Explore dApps and Smart Contracts 🌍
- Vet the dApp
Check if contracts are audited (by firms like OpenZeppelin or CertiK). Google the dev team. Use DeFiLlama to verify Total Value Locked (TVL) and community size. - Limit Permissions
Use Revoke.cash or Etherscan Token Approvals to manage dApp permissions. Never grant unlimited approvals. - Double-Check Transactions
Look closely at the recipient address, amounts, gas fees, and approval limits. Test with small amounts first. - Disconnect After Use
Always disconnect wallets when not actively transacting.
Dodge Phishing and Social Engineering Scams 🛡️
- Be Skeptical
If someone messages you unsolicited, it's likely a scam. Double-check URLs, especially on airdrops or giveaways. - Protect Your Keys
No team member, support rep, or mod will ever ask for your seed phrase. - Slow Down
Urgency is a red flag. Confirm with official sources on Discord or verified Twitter accounts before acting. - Use Anti-Phishing Tools
Browser extensions like MetaMask’s phishing detection can help detect malicious sites.
Guard Your Private Keys and Seed Phrases Like Treasure 💎
- Go Offline
Write your seed on paper or metal. Never store in Google Drive, Notion, or cloud-based notes apps. - Use Hardware Wallets
Cold wallets keep keys off the internet. Transactions are signed inside the device, keeping private keys safe. - Multiple Backups
Make two or three offline backups and store them separately in fireproof or waterproof containers. - Consider Crypto Inheritance
Use multisig wallets or trusted legal solutions to ensure your loved ones can access your crypto if needed.
Power Up with Strong Passwords and 2FA 🔐
Passwords are often the weakest link in any security setup—and in Web3, weak or reused passwords can mean instant loss of assets. Here’s how to strengthen your defenses:
- Use a Password Manager
Tools like Bitwarden or 1Password help you generate and store complex, unique passwords. - Enable 2FA
Use app-based tools like Authy or Google Authenticator, or hardware tools like YubiKey. Avoid SMS-based 2FA. - Use Strong, Memorable Phrases
Create master passwords with 16+ characters using uncommon word combos and symbols. - Avoid 2FA Phishing
Only enter 2FA codes on verified sites. Bookmark trusted domains.
✅ Web3 Security Checklist
Quick wins to keep you safe:
✅ Use a hardware wallet for large funds
✅ Back up your seed phrase offline (paper + metal)
✅ Enable 2FA (app or hardware-based)
✅ Revoke unused dApp permissions regularly
✅ Avoid clicking unknown airdrops or links
✅ Use separate browser profiles for Web3
✅ Vet dApps and smart contracts before use
✅ Use password managers and strong credentials
✅ Only use audited bridges for cross-chain transfers
✅ Have a crypto inheritance plan
Stay Ahead: Resources to Keep You Informed 📚
- Security Blogs: CertiK, SlowMist, OpenZeppelin, Immunefi
- Learning Platforms: Alchemy University, CryptoZombies, Cyfrin
- Exploit Trackers: Chainalysis, TRM Labs
- Contract Safety Tools: Revoke.cash, Blockaid
Final Thoughts: Conquer Web3 with Confidence 💪
Web3 is an incredible space, but it’s not without risks. From phishing and rug pulls to smart contract exploits and key theft, the threats are real—but so are the solutions. Secure your wallets (mix hot and cold storage), double-check dApps, protect your keys with hardware wallets, and stay skeptical of too-good-to-be-true offers.
With strong passwords, 2FA, and a habit of staying informed, you’ll be ready to explore Web3 with confidence. Raise your shield and dive into this digital frontier—your secure Web3 adventure starts now! 🌟
More About Mitosis University
Explore More Articles
From Monoliths to Modules: Why Blockchain Needs to Evolve and How Mitosis Is Leading the Way
🔍 SUCCINCT SP1 ZKVM: MAKING ZERO-KNOWLEDGE PROOFS ACCESSIBLE TO RUST DEVELOPERS

Comments ()