Mitosis's Security Measures and Lessons from Crypto Hacks

Introduction: The Importance of Security in DeFi
Protecting user assets is everything, especially for projects like Mitosis. As a Layer 1 blockchain crafted for seamless cross-chain liquidity management, Mitosis lets users pool assets into its Vaults, which are deployed across multiple networks to maximize returns for liquidity providers. Given the high value of assets it handles, ensuring robust security measures is critical to protect users and maintain trust in the ecosystem.
Mitosis: A Layer 1 for Cross-Chain Liquidity
Mitosis is an Ecosystem-Owned Liquidity (EOL) Layer 1 blockchain that aims to revolutionize DeFi by enabling efficient cross-chain liquidity management. Its flagship product, Matrix, curates premium DeFi opportunities, ensuring transparency, control, and fair participation for users. Mitosis is built on the Cosmos SDK, which provides a secure foundation for blockchain development, and uses CometBFT for consensus, a well-established mechanism in permissioned blockchains. This architecture is designed to handle the complexities of cross-chain interactions, making security a top priority as it manages significant TVL across multiple networks.
Mitosis's Security Measures
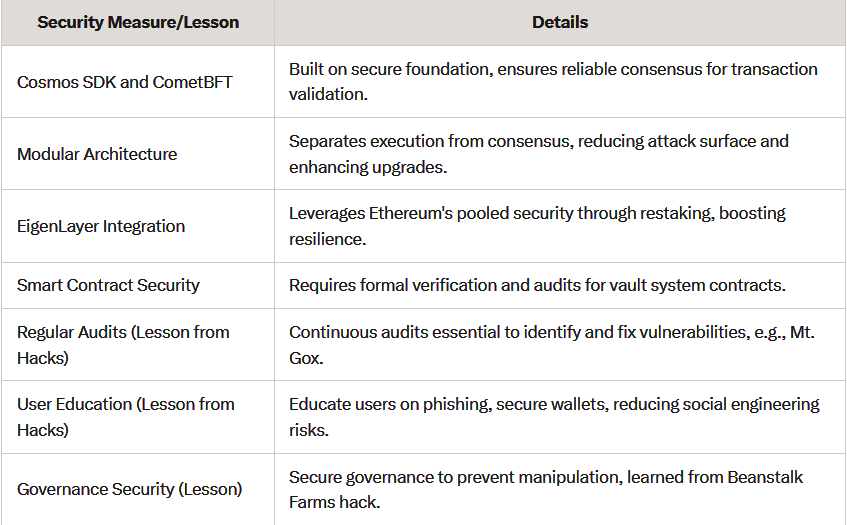
Mitosis has implemented several security measures to safeguard its ecosystem, as evidenced by its technical documentation and integration with established technologies:
- Cosmos SDK and CometBFT: Mitosis is built on the Cosmos SDK, known for its security in permissioned blockchains. CometBFT, used for consensus, ensures reliable and secure transaction validation. This choice leverages the security features inherent in these technologies, providing a strong foundation for Mitosis's operations.
- Modular Architecture: Mitosis employs a modular architecture that separates execution from consensus. This design choice allows for better security management, as it isolates potential vulnerabilities and makes it easier to upgrade or patch specific components without disrupting the entire system. This separation reduces the attack surface and enhances overall security.
- Integration with EigenLayer: A key security enhancement is Mitosis's integration with EigenLayer, a protocol that allows restaking of ETH to secure additional services. EigenLayer enables Mitosis to leverage Ethereum's robust security model, benefiting from the pooled security of Ethereum's stakers. This is particularly important for a protocol managing liquidity across multiple chains, as it ensures that security scales with the network's growth. EigenLayer's security model is based on restaking, where stakers can secure Actively Validated Services (AVSs) without compromising Ethereum's security, as detailed on the EigenLayer website (EigenLayer).
- Smart Contract Security: Mitosis's vault system relies on smart contracts deployed across supported blockchain networks for asset custody and liquidity deployment. These contracts must be securely written and regularly audited to prevent exploits. Formal verification and penetration testing are critical for such systems, ensuring they are free from vulnerabilities that attackers could exploit.
While specific audit reports for Mitosis are not publicly available, it is standard practice for such projects to undergo rigorous security audits before and after deployment. The emphasis on transparency and user control, as seen in its Matrix product, also contributes to economic security, reducing the risk of mismanagement or unauthorized access.
The Importance of Security in Blockchain Projects
Security is critical for any blockchain project, especially those handling liquidity like Mitosis. The DeFi space has seen numerous hacks over the years, resulting in billions of dollars in losses. According to a 2025 report by CCN, over $1.7 billion was stolen in crypto hacks in 2023 alone, highlighting the persistent vulnerabilities within the space (Crypto Hacks 2025). These incidents underscore the need for robust security measures and the importance of learning from past mistakes to prevent future breaches.
Learning from Past Crypto Hacks: Case Studies and Lessons
The crypto space has experienced several high-profile hacks, each offering valuable lessons on security. Below are detailed case studies of notable incidents and the lessons learned:
- Mt. Gox (2014):
- What Happened: The largest Bitcoin exchange at the time lost $460 million due to poor security practices, including not using version control for source code. Hackers exploited vulnerabilities, leading to significant financial losses and lawsuits against the company.
- Lesson: Implement best practices in software development, such as version control, regular code reviews, and penetration testing. This incident, detailed in a 2025 article by Crystal Intelligence, highlights the importance of secure coding practices (The 10 Biggest Crypto Hacks).
- KuCoin (2020):
- What Happened: Hackers stole $275 million by obtaining private keys to hot wallets. KuCoin recovered most of the funds and implemented enhanced security measures, including a new risk control system, network security upgrades, and restructuring its cybersecurity team, as outlined in a 2022 Tech Monitor article (The ten biggest crypto hacks).
- Lesson: Robust key management and quick response plans are crucial. Using multi-signature wallets and keeping large amounts of assets in cold storage can reduce risks, emphasizing the need for proactive security enhancements post-incident.
- Poly Network (2021):
- What Happened: $610 million was hacked, but the hacker returned the funds. This incident, reported by the BBC in 2021, highlighted the importance of having mechanisms to negotiate with hackers or having insurance to cover losses (The real victims of mass crypto-hacks).
- Lesson: Consider implementing insurance or compensation plans for users to mitigate the impact of hacks, ensuring user trust and financial stability.
- Beanstalk Farms (2022):
- What Happened: $80 million was stolen through a governance attack by manipulating the decentralized governance structure, as detailed in a 2023 TechTarget article (Top 9 cryptocurrency hacks of 2022). The attacker used a flash loan to accumulate tokens and pass malicious proposals.
- Lesson: Secure governance models are essential. Protocols must ensure that governance mechanisms are resistant to manipulation, such as through majority vote attacks, by implementing checks and balances.
From these incidents, several common themes emerge, as noted in a 2019 Help Net Security article (Lessons learned from the many crypto hacks):
- Regular Security Audits: Continuous auditing and penetration testing are crucial to identify and fix vulnerabilities before they can be exploited.
- Smart Contract Security: For projects like Mitosis that rely on smart contracts, formal verification and thorough testing are essential to prevent exploits.
- User Education: Educating users about phishing, social engineering, and best practices for securing their assets can prevent many attacks, reducing the risk of human error.
- Multi-Signature and Cold Storage: Using multi-signature wallets and keeping large amounts of assets in cold storage can reduce the risk of theft, especially for centralized exchanges and protocols.
- Governance Security: Ensuring that governance structures are secure and resistant to manipulation is critical for projects with decentralized decision-making, preventing attacks like those seen in Beanstalk Farms.
Additionally, Mitosis's integration with EigenLayer provides a significant security advantage. By leveraging Ethereum's pooled security, Mitosis can reduce the risk of attacks while benefiting from the established trust in Ethereum's network, as detailed on the EigenLayer website (EigenLayer).
Conclusion
Looking ahead, Mitosis's security measures, including its use of Cosmos SDK, CometBFT, EigenLayer, and modular architecture, position it well to handle the demands of cross-chain liquidity management. By learning from past crypto hacks, Mitosis can further enhance its security posture, ensuring it remains a trusted platform for DeFi users. Continuous monitoring, regular audits, and user education will be key to protecting its ecosystem and building a safer future for decentralized finance.
Mitosis continues to evolve, with its integration with EigenLayer and focus on security, making it a promising player in the DeFi space. By applying the lessons from past incidents, Mitosis can lead the way in creating a more secure and interconnected blockchain ecosystem.
You can keep in touch with MITOSIS by following:
WEBSITE || X (Formerly Twitter) || DISCORD|| DOCS


Comments ()