Nexus zkVM: Concluding the Vision for Verifiable Computation at Internet Scale
This article concludes a series exploring the Nexus project, a bold effort to bring verifiable computation to Internet scale. Previous articles have discussed the foundational concepts, early development stages, and potential applications of the Nexus ecosystem. Here, we culminate with the Nexus zero-knowledge Virtual Machine (zkVM), delving into its sophisticated architecture and how it enables the efficient proving of computations involving billions of CPU cycles. By combining a specialized computational model, advanced cryptographic techniques, and a distributed prover network, the Nexus zkVM reduces the cost of verifiable computation by orders of magnitude, paving the way for a future where digital interactions are grounded in mathematical truth.
What Are Zero-Knowledge Proofs?
Zero-knowledge proofs (ZKPs) allow one party to prove that a computation is correct without revealing the underlying data or computation details. Imagine proving you know the solution to a puzzle without showing the solution itself—ZKPs achieve this mathematically. For example, a ZKP can verify that a financial transaction is valid without disclosing the sender’s identity or amount. The Nexus zkVM leverages ZKPs to verify computations at an unprecedented scale, ensuring integrity and privacy for applications ranging from blockchain to secure data processing. This accessibility makes the Nexus zkVM relevant to developers, businesses, and end-users alike.
Why This Architecture Matters: Scalability and Efficiency
The Nexus zkVM's sophisticated architecture is a deliberate response to the long-standing challenges of proving large-scale computations efficiently with zero-knowledge proofs. By combining specialized components with a structured workflow, Nexus overcomes the practical limitations that have hindered widespread ZKP adoption, enabling the proving of computations orders of magnitude larger than previously thought possible.
The Nexus Virtual Machine (NVM): Simplicity and Security
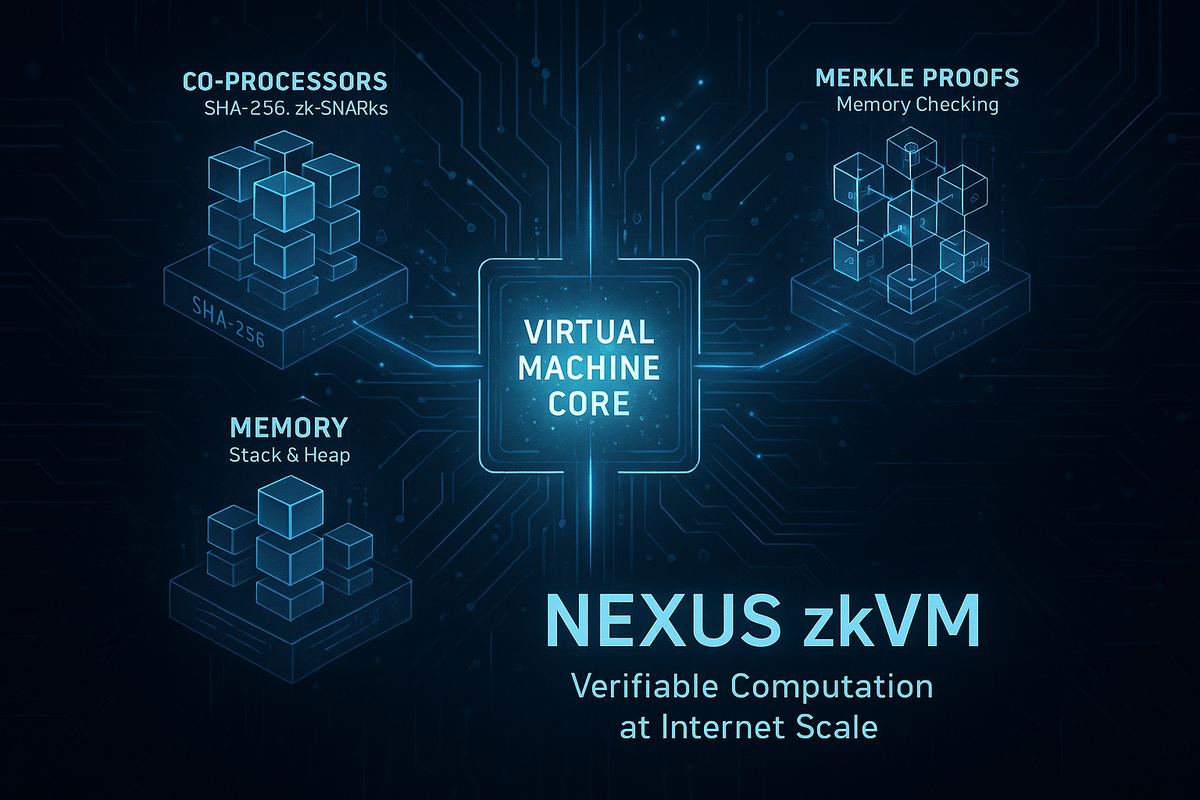
At the core of the Nexus zkVM lies the Nexus Virtual Machine (NVM)—a minimal, extensible CPU architecture purpose-built to reduce prover overhead per instruction. Unlike general-purpose ISAs like RISC-V or the EVM, which become inefficient when adapted for zero-knowledge proofs, the NVM uses a lean 32-bit instruction set with only 40 operations. This simplicity lowers the cost of proof generation and improves auditability, minimizing the risk of vulnerabilities such as unconstrained logic paths. The result is a secure, efficient foundation for scalable, verifiable computation.
zkVM Co-processors: Balancing Generality and Performance
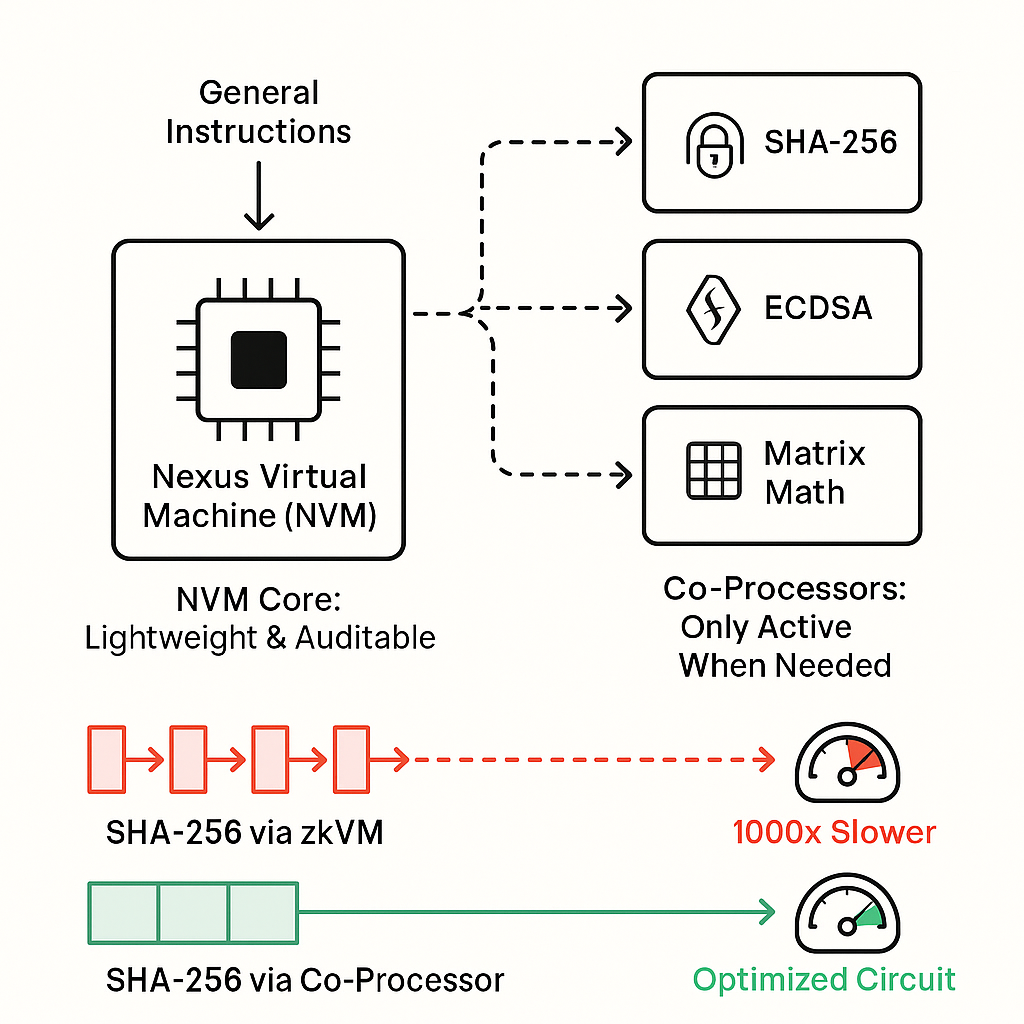
A key innovation of the Nexus zkVM is its use of zkVM co-processors, which allow developers to extend the NVM with custom instructions tailored to specific tasks, such as cryptographic operations (e.g., SHA-256 hashing or ECDSA signatures) or high-level computations like matrix multiplications. Unlike traditional zkVM designs, where adding instructions increases the proving cost for every cycle, co-processors ensure that their computational overhead is only incurred when used. For instance, proving a SHA-256 hash directly as a co-processor circuit requires roughly 1000x less computation than emulating it in a virtual machine. This hybrid approach combines the generality of a CPU model with the efficiency of ASIC-like circuits, enabling developers to optimize performance for specialized tasks without sacrificing the NVM’s simplicity.
One of the smart design choices in the Nexus zkVM is its use of co-processors—specialized modules that handle specific tasks, like cryptographic operations or heavy math, without slowing down the rest of the system. Think of the NVM as a simple, reliable engine, and co-processors as turbochargers you attach only when needed.
Take SHA-256 as an example. It’s a cryptographic hash function used almost everywhere in Web3—from verifying transactions and checking data integrity to securing wallet addresses. In traditional zkVMs, proving that a SHA-256 hash was correctly computed can be painfully slow and expensive because the virtual machine has to simulate each tiny step of the hash function, one instruction at a time.
With Nexus, instead of simulating all those steps, a SHA-256 co-processor can do the same work in a single, optimized circuit—making proof generation about 1000 times faster. This means developers can include advanced features like secure data checks or proof-of-identity inside their apps, without worrying about huge costs or long proving times.
This hybrid approach—simple virtual machine plus efficient co-processors—lets Nexus keep its system light and flexible while handling heavy tasks when needed.
Developer-Friendly Experience
The Nexus zkVM prioritizes a seamless developer experience, allowing programmers to write verifiable applications in Rust—a widely adopted, high-performance language—without needing deep expertise in zero-knowledge cryptography. Simple commands like cargo nexus prove and cargo nexus verify integrate proof generation and verification into standard development workflows, as demonstrated by the whitepaper’s example of proving a Fibonacci function in Rust. This accessibility empowers developers to focus on building applications, such as privacy-preserving smart contracts or secure data analytics, rather than grappling with the complexities of ZKP systems.
Staged Execution for Optimal Proving
The zkVM’s execution sequence is meticulously organized into four stages to optimize the proving process:
- Compilation: Programs are compiled to the NVM’s instruction set, supporting architectures like RISC-V, EVM, or WebAssembly (Wasm) through emulation or custom extensions.
- Execution: The NVM executes the program, generating a full execution trace.
- Folding: Incremental proofs are generated and accumulated in a massively parallelized manner using advanced folding and accumulation schemes (e.g., Nova, CycleFold, HyperNova). This stage, the core of scalability, avoids expensive SNARK recursion for intermediate steps and is distributed across the Nexus Network.
- Compression: A recursive sequence of (zk)-SNARKs compresses the large accumulated proof into a succinct, easily verifiable final proof, ensuring efficient verification.
This structured workflow allows the zkVM to handle immense computational loads while maintaining fast verification times. Read more from previous article.
The Nexus Network: A Distributed Proving Powerhouse
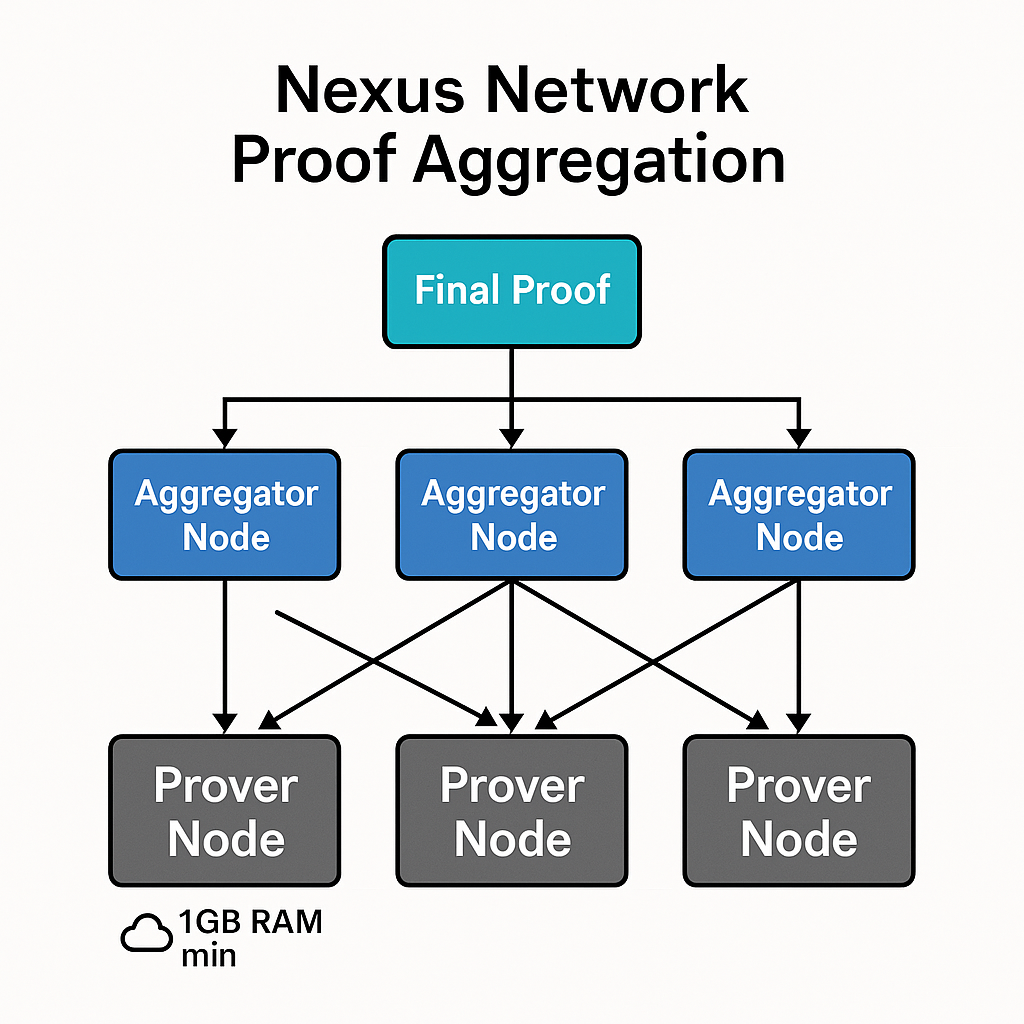
The Nexus Network aggregates the collective CPU and GPU power of a heterogeneous computer network, enabling massively parallelized proof generation. By partitioning computations into small, parallelizable chunks, the network allows devices ranging from powerful GPU clusters to laptops and even smartphones with as little as 1GB of RAM to contribute compute power. This inclusivity maximizes participation, making the Nexus Network a truly global resource. The network operates like a verifiable supercomputer, aggregating proofs in a tree-like fashion to scale the zkVM’s throughput proportionally to the collective computing power. Future implementations may introduce incentives, such as rewards for compute contributions, to sustain and grow this distributed ecosystem.
Real-World Applications
The Nexus zkVM’s ability to prove large computations efficiently opens the door to transformative applications across industries. In decentralized finance (DeFi), it can prove the correctness of complex smart contract executions, ensuring trustless financial transactions at scale. In supply chain management, it can verify the integrity of data across global networks, proving that goods have followed compliant paths without revealing sensitive details. Additionally, the zkVM’s support for Rust programs enables developers to, such as secure voting systems that guarantee accurate vote counts without disclosing individual votes, or confidential machine learning models where computations are verified without exposing proprietary data. These use cases demonstrate how the Nexus zkVM can power production-grade applications, aligning with its goal of enabling verifiable computation at Internet scale.
Current Limitations and Future Work
While the Nexus zkVM represents a significant leap forward, it is still evolving. The current implementation supports fully uniform Incrementally Verifiable Computation (IVC) but not non-uniform IVC, which is under development to enhance flexibility for custom computations. Additionally, I/O support for external data (e.g., JSON files) is not yet available but is planned for near-term updates. These improvements will further solidify the zkVM’s ability to handle diverse, real-world applications, making it an even more robust platform for developers and businesses.
Conclusion: Enabling Verifiable Computation at Scale
The Nexus zkVM, built on nearly 40 years of zero-knowledge research, is a fast, scalable platform that ensures computational integrity. It overcomes trust and fragmentation issues in verifiable tech, proving trillions of CPU cycles per second. This could enable secure, transparent elections, private data sharing for research, and fraud-proof financial systems, boosting efficiency and global cooperation through mathematical trust. The Nexus project, with its simple NVM, distributed Nexus Network, and recursive proofs, ensures data and computation integrity. This final piece on the Nexus ecosystem highlights the zkVM’s role in fostering human cooperation through undeniable mathematical truth in digital interactions.
Source
Nexus whitepaper-https://whitepaper.nexus.xyz/
Similar Articles
Powering Nexus: How Folding Schemes Scale Verifiable Proofs
Laying the Foundation: 'The One-Time Setup' for Nexus zkVM Architecture
Scaling Verifiable Computation: The Nexus Network, A Verifiable Supercomputer
The Nexus Virtual Machine (NVM): A Finely Tuned Engine for Verifiable Computation
zk‑SNARKs to zk‑STARKs: The Evolution of Zero‑Knowledge in Web3
Succinct SP1 zkVM: Democratizing Zero-Knowledge Proofs for Rust Developers
🧬 How Replacing the EVM with RISC-V Could Accelerate Mitosis’ Programmable Liquidity Vision
The Future of Web3 Security: Verifiability Without Visibility Using zkTLS and FHE
Unpacking Blockchain's Engines: A Comprehensive Look at Virtual Machines


Comments ()