Nexus ZKVM: Enabling Verifiable Compute at Internet Scale

Introduction
As DeFi scales and modular blockchains multiply, the need for fast, verifiable computation has become more than an academic challenge — it’s a prerequisite for trustless infrastructure at the global level. With the final design of Nexus ZKVM now published, Mitosis marks a major milestone in delivering this capability at Layer 1.
This article explores the architecture, purpose, and system-level implications of Nexus ZKVM, and how it enables verifiable compute as a native primitive on Mitosis — unlocking zero-knowledge infrastructure that doesn’t compromise on decentralization, scalability, or usability.
The Problem: Modular Fragmentation and Trusted Execution Assumptions
Modern blockchain design favors modularity. From L2 rollups to app-chains and sovereign execution environments, compute is increasingly split across vertical layers. But modularity creates surface area. Every bridge, sequencer, and settlement pipeline must be trusted or verified.
Today, most L1s depend on offchain actors or trusted hardware (e.g., TEEs) to verify compute. This breaks the chain of trust, and introduces risk that compromises core DeFi composability and sovereignty.
Enter Nexus ZKVM
Nexus ZKVM is Mitosis' native ZK virtual machine — purpose-built to offer fully verifiable offchain computation with direct integration into Mitosis' cross-chain architecture.
Core Objectives:
- Trustless Compute: Eliminate the need for external verifiers or centralized sequencers.
- Universal Compatibility: Support a wide range of ZK backends and proving systems.
- Composable Interoperability: Plug into the modular stack with intent-based messaging.
With Nexus, users can validate complex logic, simulate execution outcomes, or anchor offchain ML inference — and do so with cryptographic assurance.
Verifiable Compute Flow on Mitosis
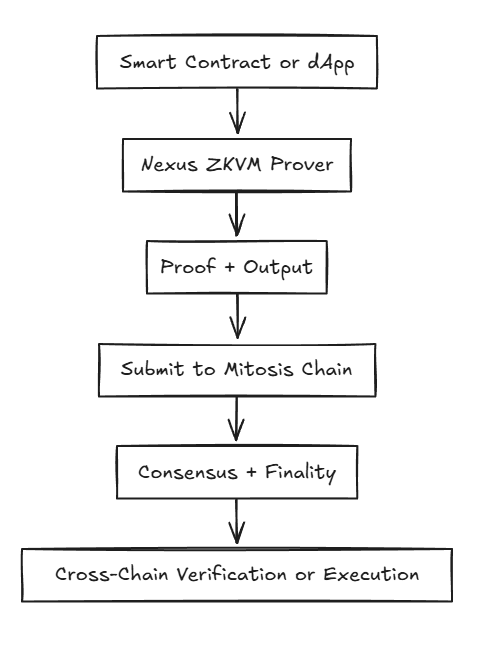
Why This Matters
Nexus ZKVM is not just about "doing compute." It’s about proving that compute was done correctly, without relying on central authorities. That unlocks a number of use cases:
- Privacy-preserving data proofs in DePIN and healthcare
- ZKML inference for decentralized AI services
- High-integrity bridges that don’t require multisigs or trusted setups
- Automated legal contracts and proofs of identity without centralized databases
It’s the foundation for a verifiable internet — and Mitosis is positioning itself as the base layer.



Comments ()