Preventing the Next KiloEx: How Mitosis Can Avoid Cross-Chain Oracle Exploits

On April 14, 2025, KiloEx, a decentralized trading platform, suffered a catastrophic exploit resulting in $7.5 million in losses. The breach stemmed from a critical flaw in the platform’s oracle access control, allowing a malicious actor to manipulate asset prices and siphon funds across multiple chains. As Mitosis continues to expand as a cross-chain modular liquidity protocol, understanding the lessons of KiloEx is crucial for building a resilient DeFi ecosystem.
🔍 What Happened at KiloEx: A Technical Recap
⚠️ The Root Vulnerability: Oracle Access Control Flaw
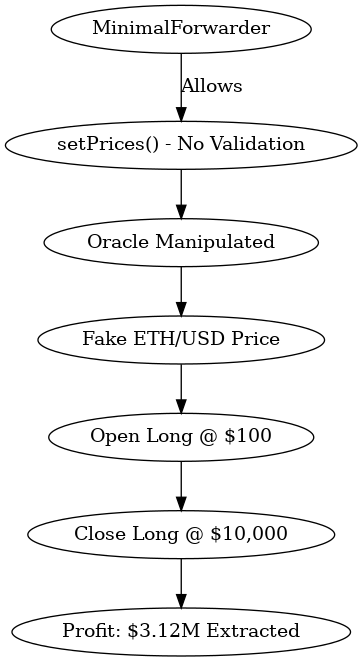
At the core of the exploit was the MinimalForwarder contract. It lacked robust access controls, allowing unauthorized actors to call privileged functions like setPrices in the KiloPriceFeed contract. This design oversight meant anyone could arbitrarily set prices used by the protocol to execute trades.
⚖️ Exploit Mechanics
- Price Manipulation: The attacker set ETH/USD to $100 to open a long, then raised it to $10,000 to close, extracting $3.12M in one transaction.
- Cross-Chain Abuse: The attack was executed across Base, opBNB, and BSC.
- Settlement Exploitation: KiloEx’s on-chain finality locked in profits immediately.
- Obfuscation Tools: Tornado Cash was used for funding, and zkBridge and Meson facilitated asset movement across chains.
🚫 Fallout and Response
- Token Crash: KILO fell over 30% within 24 hours.
- Full Pause: Trading and liquidity operations were suspended.
- Bounty Resolution: The attacker returned all stolen funds for a 10% white-hat bounty ($750,000).
📉 Implications for Modular DeFi Protocols
KiloEx’s failure highlights systemic vulnerabilities in:
- Oracle permissioning
- Cross-chain synchronization
- Smart contract access control
- Transparency and crisis communication
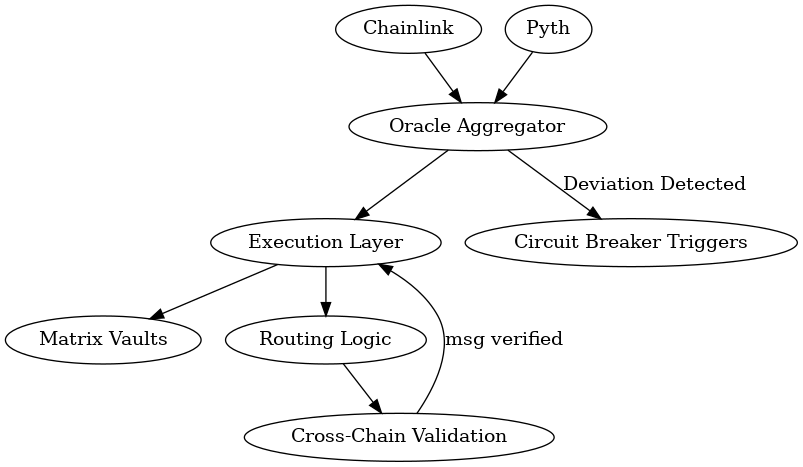
As Mitosis powers cross-chain liquidity with components like Matrix Vaults and Execution Layers, it must proactively implement advanced security measures.
⚖️ Mitosis: Strengthening Defense Against Oracle Exploits
1. 🔒 Harden Oracle Architecture
- Decentralized Feeds: Integrate trusted providers like Chainlink, Pyth Network, or RedStone.
- Redundant Validation: Use median or multi-feed consensus to detect anomalies.
- No Single Points: Avoid any update logic that relies on a single forwarder or admin.
📄 Related Docs: Execution Layer Overview
2. 🛡️ Enforce Role-Based Access Control
- Multisigs & AccessControl: Use OpenZeppelin libraries and Gnosis Safe for sensitive functions like
updateVaultParams,setOracle, andexecuteRoute. - Verify Senders & Originators: Ensure proper checks for both
msg.senderandtx.origin, unlike the failed MinimalForwarder model.
📄 Matrix Vault Docs: Admin Permissions
3. 🌐 Secure Cross-Chain Communication
- Message Validation: Validate cross-chain messages from LayerZero, Hyperlane, or other sources to ensure trusted origin.
- Circuit Breakers: Temporarily pause suspicious transfers or trades during price anomalies.
- Standardized Protocols: Maintain consistent rules and access layers across Base, Arbitrum, Mantle, BNB, and other networks.
📄 Read: Bridge Layer Details
4. ⚡ Real-Time Monitoring & Oracle Deviation Alerts
- Use systems like Cyvers, Forta, or custom tooling to:
- Detect rapid price fluctuations
- Trigger alerts on abnormal trading activity
- Pause transactions during oracle feed outliers
5. 📨 Transparent Incident Response & Compensation
- Emergency Reserve Fund: Backstop losses from critical failures.
- Bug Bounty Program: Incentivize responsible disclosure via platforms like Immunefi.
- Postmortem Playbook: Publish immediate post-incident reports, including attack vector, resolution timeline, and fixes.
6. 🎓 Educate and Empower Users
- Offer dashboards and tutorials on cross-chain risks, wallet security, and oracle dependence.
- Encourage users to diversify funds and monitor contracts they interact with.
📚 Visual Summary
🏙️ KiloEx Exploit Flow
📊 Mitosis Defensive Architecture
🚀 Conclusion
The KiloEx incident offers a wake-up call to DeFi platforms operating across chains. Mitosis is well-positioned to avoid similar catastrophes by building a multi-layered security architecture, adopting decentralized oracle feeds, enforcing rigorous access control, and preparing real-time threat detection and incident response systems.
With the right strategy, Mitosis can become a blueprint for secure, composable, and resilient cross-chain liquidity infrastructure.
📄 Explore more at university.mitosis.org and docs.mitosis.org


Comments ()