Smart Permissions: Unlocking Secure Automation for Crypto and Beyond

The Newton Protocol, developed by the Newton Foundation, is a verifiable automation layer designed to transform onchain finance by addressing the fragmentation, manual workflows, and trust barriers that hinder mainstream crypto adoption. By enabling "application abstraction"—where users express high-level goals like "maximize my stablecoin yields across chains" and intelligent agents handle the complexity—Newton lays the groundwork for a user-driven onchain economy, encompassing agentic finance and programmable commerce. At the heart of this vision lies zkPermissions, a foundational solution that leverages zero-knowledge proofs (ZKPs) to provide secure, granular, and verifiable control over automated actions, ensuring users can safely delegate tasks without relinquishing control or compromising privacy.
The Need for Verifiable Automation

The crypto ecosystem faces significant challenges: broken user experiences, underutilized capital, and risky automation. The litepaper notes that only ~40% of capital in decentralized finance (DeFi) is actively deployed, with over $1 trillion potentially remaining idle by 2030 if fragmentation persists. Existing automation solutions, such as Telegram bots, often require users to surrender private keys, exposing them to hacks and phishing risks. Moreover, the rise of AI agents in crypto finance demands secure execution and protocol-level trust to prevent issues like hallucinated actions. zkPermissions address these problems by turning automation into a provable, trust-minimized primitive, much like Chainlink brought offchain data onchain, enabling verifiable offchain computation and automation for Web3.
How zkPermissions Work
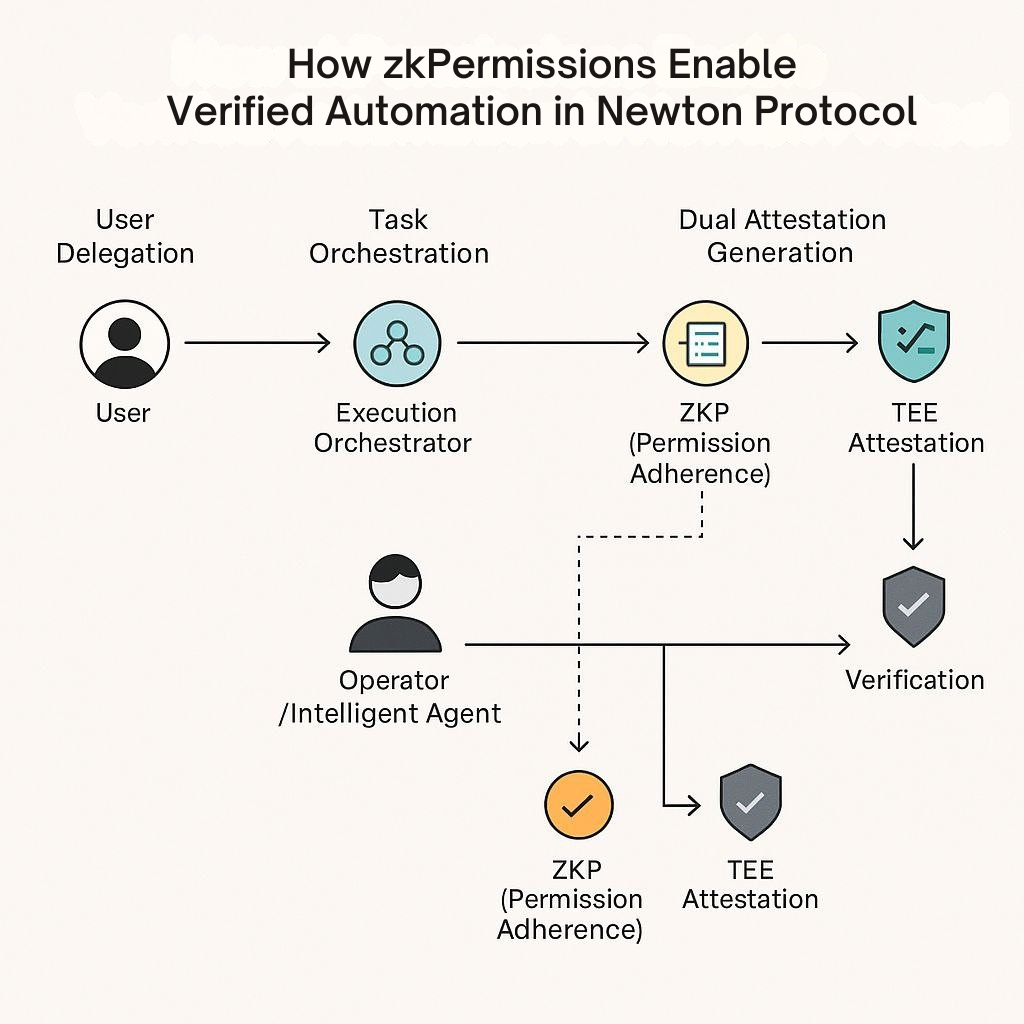
zkPermissions allow users to encode specific rules and constraints into a zero-knowledge circuit, bound to a session key used by automated agents. This circuit enables a "prover" (the agent) to convince a "verifier" (the protocol or another party) that an action adheres to the defined permissions without revealing the underlying logic or data. This ensures privacy and trust minimization, as users can delegate tasks with precise boundaries enforced cryptographically. The Newton Protocol integrates zkPermissions within a broader architecture that includes:
- Smart Accounts: Programmable accounts that offload execution to agents via session keys, with permissions updatable or revocable at any time.
- Execution Orchestrator: An orderbook-based marketplace that matches user automation intents (e.g., "rebalance my portfolio weekly") with operators, supported by validators who verify execution proofs.
- Trusted Execution Environments (TEEs): Hardware-based enclaves (e.g., Intel TDX) that ensure trusted computation, generating attestations alongside ZKPs to verify offchain execution.
- Minimal App-Specific Rollup Design: Optimizes performance and security for scalable automation.
For every action, operators must submit a ZKP attesting that the execution adhered to the zkPermission, complemented by a TEE attestation proving the task ran in a secure environment. This dual-verification model ensures trust and scalability, with intensive computation performed offchain and verified onchain.
Flexible and Programmable Rules
zkPermissions are highly flexible, enabling users to define granular constraints across several categories, as outlined in the Newton litepaper:
- Data-Driven Execution Conditions: Permissions tied to real-time or historical data feeds, such as allowing a swap only if onchain sentiment indicates bullish conditions, executing a trade if a 15-minute moving average crosses above a 1-hour moving average (golden cross), or authorizing staking only if gas fees are below 20 gwei, funding rates are positive, and L2 transaction volume exceeds $100M in 24 hours. Real-world events, like Consumer Price Index (CPI) data signaling inflation below 2%, can also trigger actions.
- Risk and Price Sensitivity Checks: Permissions based on market volatility or price deviations, such as permitting execution only if an implied volatility index (e.g., DVOL) is below 30, buying if the price is two standard deviations below a 7-day moving average and RSI < 30 (oversold), or triggering a sell if the price deviates ±5% from an oracle median. Multi-block safety checks can require conditions to hold for consecutive blocks.
- Transaction Volume and Timing Constraints: Limits on transaction scope and timing, such as capping total volume at $500 USD per execution, allowing three executions daily if the Time-Weighted Average Price (TWAP) is within 1% of the Volume-Weighted Average Price (VWAP), or restricting execution to Mondays between 8 AM and 12 PM UTC.
- Default and Baseline Permissions: Standard safeguards for all agents, including spending limits, expiration dates, and token allowlists.
These composable rulesets act like building blocks, allowing developers to stack and assemble custom policies using onchain and offchain data sources, such as blockchain analytics, oracle feeds, or verifiable credentials.
Newton’s Ecosystem: Participants and Dynamics
zkPermissions operate within a decentralized automation marketplace coordinated by four participant roles:
- Developers: Build automation agents, from simple scripts to AI-driven models, using Newton’s SDKs and zkML frameworks. These agents are secured with TEEs and ZKPs, ensuring verifiable execution without revealing proprietary logic.
- Operators: Run automation services, competing to fulfill user tasks efficiently and earning fees. They build reputation through verifiable performance, with economic penalties (e.g., slashing) for misbehavior.
- Users: Submit automation intents via intuitive interfaces, defining permissions and delegating tasks to trusted agents. Future iterations will allow users to rate operators, enhancing marketplace transparency.
- Validators: Secure the protocol via delegated proof-of-stake (dPoS), verifying blocks and execution proofs for fast finality.
This ecosystem creates a flywheel effect: a seamless user experience attracts more users, driving demand for diverse agents, incentivizing better operators, and rewarding trusted execution, fostering a merit-based economy for verifiable automation.
Applications in Web3
zkPermissions are fundamental to Newton’s vision of onchain finance, enabling users to delegate complex tasks securely. Key use cases include:
- Cross-Chain Automated Strategies: Execute recurring token purchases, liquidity provision, or portfolio rebalancing with cryptographic stop-losses, caps, and whitelists.
- Automated Vault & Risk Management: Monitor collateralization ratios and trigger repayments or reallocations to minimize liquidation risks.
- Verifiable Copy Trading Networks: Mirror trades from lead traders within user-defined limits on position size, pairs, and slippage.
- Programmable Stablecoin Commerce: Automate payments, recurring billing, or metered services with compliance checks and spending limits.
- DAO Treasury Operations: Delegate yield optimization or contributor payments to verifiable agents governed by multi-party zkPermissions.
- Custodial Compliance: Define provable delegation rules for custodians, ensuring KYC/AML compliance without surrendering key control.
- AI-Governed Trading Agents: Deploy AI models as zk-circuited agents, with every inference verified onchain, addressing the critical need for secure crypto AI primitives.
By enabling these use cases, zkPermissions mitigate risks associated with untrusted bots and unlock the next phase of Web3 adoption.
Applications Beyond Web3
The concept of verifiable, privacy-preserving permissions extends to traditional industries:
- Secure Access Control: In enterprise systems, zkPermissions could prove authorization for data access without revealing user details, reducing attack surfaces.
- Automated Compliance and Auditing: Regulated industries could use zkPermissions to prove data processing complies with GDPR or CCPA within TEEs, streamlining audits.
- Delegation in Complex Systems: Large organizations could delegate specific tasks with cryptographically enforced boundaries, ensuring auditable compliance.
- Secure AI Model Execution: zkPermissions could define operational constraints for AI in healthcare or finance, proving adherence to ethical guidelines without exposing model parameters.
Developer Tooling and Extensibility
Newton empowers developers with robust tooling to build and extend automation agents. SDKs enable the creation of zkPermissions as composable rulesets, supporting historical flow-of-funds analysis, real-time oracle feeds, and dynamic allowlists. The zkML framework allows developers to circuitize offchain services and AI models into verifiable agents, defining input/output formats and execution costs. This extensibility ensures developers can rapidly deploy secure, scalable agents, fostering innovation across financial and commercial verticals.
Development Roadmap
Newton prioritizes user safety, trust, and usability. The initial rollout focuses on simple automations, like recurring token purchases, executed in TEEs with baseline zkPermissions for accessibility. Future phases will:
- Expand to advanced zkPermission frameworks for expressive rules.
- Implement full marketplace mechanics for human-to-agent and agent-to-agent interactions.
- Enhance developer tooling to simplify agent creation.
This phased approach ensures a secure foundation while scaling to a decentralized automation economy.
Background and Context
Newton builds on the success of Magic, co-founded in 2018 by Sean Li and Jaemin Jin, who bring expertise from Kitematic (acquired by Docker) and Uber. Magic pioneered embedded wallets, onboarding over 50 million wallets and powering 2 million monthly active wallets for platforms like Polymarket and Immutable. With $90 million raised from investors like PayPal Ventures and Polygon, Newton is well-positioned to address the trust and usability gaps in Web3 automation.
Conclusion
zkPermissions transform permissions into a verifiable, privacy-preserving primitive, enabling granular control in automated systems. Integrated within Newton’s architecture, they empower users to delegate complex tasks securely, developers to build extensible agents, and operators to execute reliably, all within a reputation-driven marketplace. By addressing fragmentation, security risks, and usability challenges, zkPermissions pave the way for scalable crypto adoption, both in Web3 and beyond, creating a future where trust is built into every transaction.
Reference
Newton litepaper
Similar Articles
zk‑SNARKs to zk‑STARKs: The Evolution of Zero‑Knowledge in Web3
Succinct SP1 zkVM: Democratizing Zero-Knowledge Proofs for Rust Developers
🧬 How Replacing the EVM with RISC-V Could Accelerate Mitosis’ Programmable Liquidity Vision
The Future of Web3 Security: Verifiability Without Visibility Using zkTLS and FHE
Unpacking Blockchain's Engines: A Comprehensive Look at Virtual Machines



Comments ()