The Agent Economy: Building Trust and Reputation Through Verifiable Execution

As explored in a prior article, the Newton Protocol, developed by the Newton Foundation and leveraging Magic’s expertise—having onboarded over 50M embedded wallets—addresses Web3’s fragmentation and trust barriers through “application abstraction,” where users set goals like “maximize stablecoin yields” and agents manage complexity. Powered by zkPermissions, which use Zero-Knowledge Proofs (ZKPs) for secure automation, Newton fosters a user-driven onchain economy. This article examines Newton’s “agent economy,” a decentralized marketplace where verifiable agents execute tasks, operators earn reputations, and trust is cryptographically ensured, transforming finance and beyond.
How the Agent Economy Works
Newton’s marketplace, likened to a decentralized Uber for financial tasks, coordinates four roles via the Execution Orchestrator. Users interact through an intuitive client interface, browsing agents like an OpenAI operator for seamless task delegation
- Users submit automation orders with fees, defining boundaries via zkPermissions—zero-knowledge rules enforcing constraints, e.g., “only swap if pool liquidity exceeds $10M and slippage is under 0.5%”.
- Developers build agents, from scripts to AI models, using SDKs and zkML frameworks to create verifiable, secure services rapidly.
- Operators run agents in Intel TDX enclaves, submitting TEE attestations (proving trusted execution) and ZKPs (verifying zkPermission adherence).
- Validators verify proofs via delegated proof-of-stake, finalizing actions through session keys.
The Executor stores zkPermissions, ensuring cross-chain enforcement. Operators build reputations based on execution history, success rates, and feedback, with slashing for dishonesty.
Economic Model
The agent economy thrives on aligned incentives. Users pay fees per automation order, set dynamically based on task complexity and market demand. Operators earn these fees, incentivizing efficient execution. High-performing operators gain reputation, attracting more orders, while slashing ensures accountability. This creates a flywheel: user demand spurs developers to create diverse agents, drawing more users and scaling the marketplace .
The chart below visualizes these interactions:
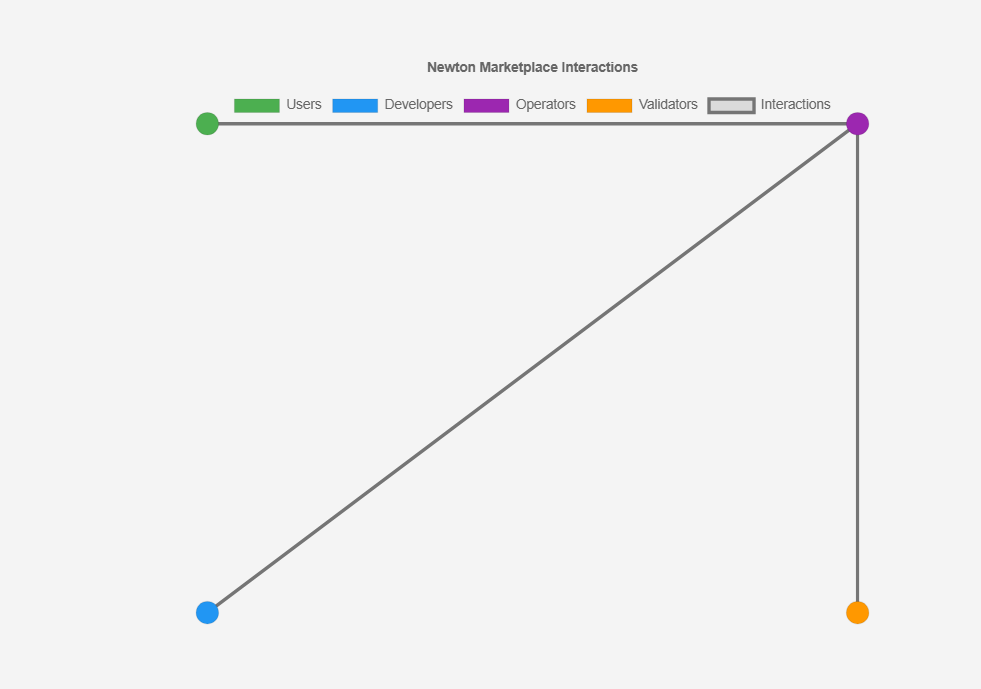
The chart, above illustrates the relationships between key participants in Newton Protocol’s decentralized automation marketplace. Represented as a scatter chart, it features four colored points: Users (green), Developers (blue), Operators (purple), and Validators (orange). Grey lines connect these points, showing how Users and Developers engage with Operators to execute automation tasks, while Validators ensure trust by verifying actions. This visual captures the collaborative dynamics driving Newton’s agent economy, where reputation and verifiable execution foster seamless onchain interactions.
Why Verifiable Execution Matters
Unlike Telegram bots, which risk hacks via private keys, or other Web3 automation protocols relying on less verifiable offchain relayers, Newton’s ZKPs and TEEs ensure trust-minimized automation, akin to Chainlink’s offchain data integration. Slashing mechanisms penalize operators for malicious actions, while zkPermissions enforce precise rules, e.g., “only trade if gas fees <20 gwei”. Its pragmatic design, using app-specific rollups, balances scalability and security. However, ZKP computation is intensive, and TEEs may face side-channel vulnerabilities.
Why Verifiable Execution Matters
Verifiable execution is a cornerstone of Newton Protocol’s mission to drive Web3 adoption by addressing the trust gap in automation. Unlike Telegram bots, which expose users to hacks by requiring private key access, or other Web3 automation protocols that rely on less verifiable offchain relayers, Newton leverages Zero-Knowledge Proofs (ZKPs) and Trusted Execution Environments (TEEs) to ensure trust-minimized automation—similar to how Chainlink brought verifiable offchain data onchain. This approach eliminates blind trust, offering cryptographic guarantees that every action aligns with user intent. For users, this means enhanced security and transparency, as they can independently verify agent behavior without relying on intermediaries. Slashing mechanisms further enforce accountability by economically penalizing operators for malicious actions, while zkPermissions enforce granular rules, such as “only trade if gas fees <20 gwei”, ensuring precision in execution. Developers benefit by building on a secure foundation, confident their agents operate within provable constraints, while operators are incentivized to maintain integrity to avoid penalties and build reputation. Newton’s pragmatic design, using app-specific rollups, balances scalability and security, making it feasible to handle complex, cross-chain workflows. However, challenges remain: ZKP computation can be resource-intensive, potentially slowing execution, and TEEs may face side-channel vulnerabilities, though Newton mitigates these through hardware-based assurances and ongoing improvements. By prioritizing verifiability, Newton not only protects users but also sets a new standard for automation in decentralized systems, enabling a future where trust is built into every transaction.
Applications in Web3
Verifiable agents streamline Web3 with:
- Cross-Chain Strategies: Recurring purchases or liquidity provision with stop-losses.
- Copy Trading: Mirror trades within position or slippage limits.
- AI Trading Agents: AI adjusts strategies, verified onchain.
- DAO Treasury: Automate yield optimization with multi-party zkPermissions.
- Custodial Compliance: Enforce KYC/AML rules without key surrender.
- Stablecoin Commerce: Automate payments or billing with compliance checks.
- Vault Management: Monitor collateral ratios, triggering repayments to avoid liquidations.
The marketplace fosters agent discovery, enabling an efficient onchain economy.
Applications Beyond Web3
Though speculative, Newton’s framework could extend to:
- Manufacturing: Agents ensure robots follow safety protocols, e.g., zkPermissions verify OSHA compliance.
- Infrastructure: AI manages grids, with ZKPs proving voltage limit adherence.
- Business Processes: Agents analyze data, with TEEs securing GDPR-compliant processing.
- Data Management: Personal agents manage identities, e.g., “only share with KYC-verified services.”
Future Outlook
Newton’s initial rollout offers simple automations (e.g., token purchases) with baseline zkPermissions. Future phases include advanced zkPermissions, agent-to-agent interactions, and enhanced SDKs (Litepaper, p. 14). Challenges include fielding user education and regulatory compliance, such as KYC/AML for Web3 finance or GDPR/CCPA for non-Web3 data processing, requiring robust zkPermissions for provable adherence. Newton could democratize DeFi and set automation standards.
Conclusion
Newton’s agent economy, driven by ZKPs, TEEs, and reputations, embeds trust in every transaction. Despite ZKP overhead, its extensible design scales crypto adoption, redefining automation within and beyond Web3.
Source: Newton Foundation Litepaper, April 27, 2025
Similar Articles
zk‑SNARKs to zk‑STARKs: The Evolution of Zero‑Knowledge in Web3
Smart Permissions: Unlocking Secure Automation for Crypto and Beyond

Comments ()