The Bridge Graveyard: How Mitosis Learns from Billion-Dollar Hacks for Your Security

1. Introduction
The Dark Side of Cross-Chain: The Epidemic of Bridge Hacks
Interoperability (cross-chain) is the Holy Grail for Web3. The ability to seamlessly move assets and data between different blockchains paves the way for a truly global and interconnected decentralized economy. However, this road to a bright future is littered with the wreckage of hacked bridges and the tears of investors who have lost hundreds of millions, if not billions, of dollars.
Ronin Bridge (624M), PolyNetwork (611m), Wormhole (326M), HarmonyHorizonBridge (100M), Nomad Bridge (190M) - these names have become synonymous not only with technological breakthroughs but also with catastrophic vulnerabilities. Each such hack is not just a financial loss; it's a blow to the trust in the entire industry, slowing down the mass adoption of DeFi and Web3 technologies. The statistics are relentless: cross-chain bridges regularly become the primary target for the most sophisticated and devastating cyberattacks.
Common Vulnerabilities: Why Do Bridges "Fall" So Often?
Analyzing these high-profile incidents reveals a number of common vulnerabilities and weaknesses that hackers have exploited:
- Private Key Compromise: Centralized storage or an insufficient number of validators whose keys need to be compromised to gain control over the bridge.
- Smart Contract Logic Errors: Vulnerabilities directly in the bridge's code, allowing bypass of checks or state manipulation.
- Input Validation Issues: Insufficient verification of messages or events from other chains.
- Attacks on External Dependencies: Vulnerabilities in oracles or other components on which the bridge's operation depends.
- Social Engineering and Operational Errors: The human factor leading to key leakage or incorrect configuration.
These recurring patterns point to systemic problems in the design and security approaches of many existing cross-chain solutions.
Mitosis: Designing Security "From the Ground Up"
Against this grim backdrop, Mitosis sets itself the task not just of creating "another" protocol for moving liquidity, but of building a fundamentally more secure and resilient infrastructure. The Mitosis team carefully studies the lessons of the past to avoid repeating others' mistakes.
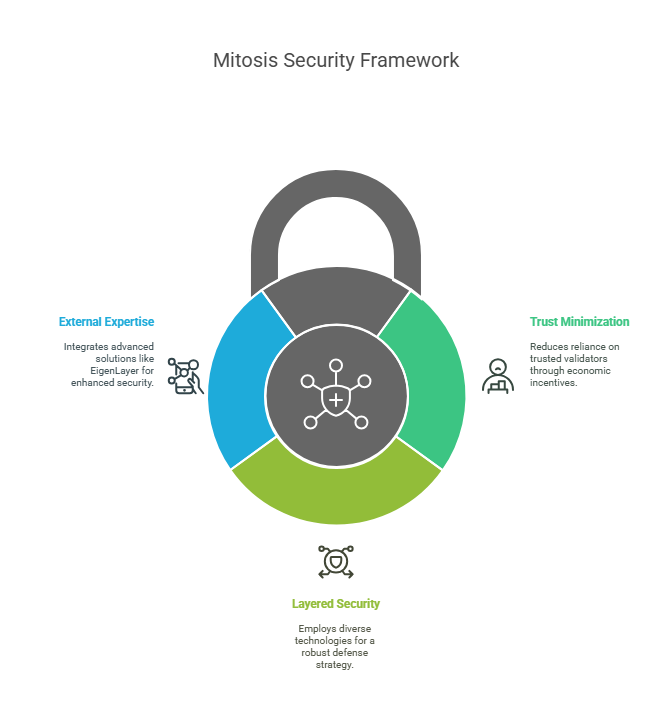
Mitosis's approach to security is based on several key principles that directly address the identified vulnerabilities:
- Trust Minimization: Instead of relying on a small group of trusted validators, Mitosis uses mechanisms based on verifiable economic incentives.
- Layered Security: A combination of different technologies and approaches to create a defense-in-depth strategy.
- Leveraging External Expertise and Technologies: Integration with cutting-edge solutions like EigenLayer AVS to borrow the cryptoeconomic security of Ethereum.
The Goal of This Article: Analysis and Solutions
In this article, we won't just list hacks. Our goal is deeper:
- To analyze several significant attacks on cross-chain bridges, highlighting the specific vectors and reasons for the hackers' success.
- To show how the architectural decisions and security mechanisms embedded in Mitosis (such as the use of EigenLayer AVS, the EOL model, and its approach to message passing) are intentionally designed to prevent or significantly complicate similar attacks.
We aim to demonstrate that Mitosis is not just talk about security, but a well-thought-out system built with the bitter experience of the entire industry in mind.
2. Attack Analysis and Mitosis's Defense Mechanisms
Let's examine some high-profile cross-chain bridge hacks and analyze what lessons Mitosis has learned from them in designing its system.
Case 1: Validator Compromise (Examples: Ronin Bridge, Wormhole)
- How It Happened:
- Ronin Bridge (Axie Infinity): Attackers gained control over 5 out of 9 Ronin network validators. This was enough to withdraw funds, as 5 signatures were required to confirm a transaction. The compromise was made possible through social engineering and exploiting a vulnerability in an RPC node of one validator, which then allowed access to other validators via a pre-existing permission.
- Wormhole (before security update): In an earlier version, Wormhole's security relied on a network of 19 "Guardians." An attacker exploited a smart contract vulnerability that allowed them to forge Guardian signatures and mint unbacked "wrapped" ETH (wETH) worth $326 million. While not a direct key compromise, it demonstrates the risk associated with trusting a limited set of validators and potential flaws in their interaction logic.
- Lessons and How Mitosis Addresses This:
- The Problem: Reliance on a small number of trusted validators creates a single point of failure. Compromising even a part of them can lead to disaster.
- Mitosis Solution (EigenLayer AVS): Mitosis integrates Actively Validated Services (AVS) from EigenLayer. This means the security of its cross-chain messages is ensured not by a small group of its own validators, but by a broad, decentralized set of AVS operators who restake their ETH.
- Economic Incentive: AVS operators risk their primary ETH stake. Malicious actions will lead to their ETH being "slashed" (lost), making an attack economically unviable.
- High Cost of Attack: To compromise a system secured by AVS, an attacker would need to gain control over a huge share of restaked ETH, which is an extremely expensive and complex task compared to attacking a few keys of a regular bridge.
- Decentralization: The set of AVS operators is significantly larger and more diverse than a typical bridge validator set, increasing resilience to censorship and collusion.
Case 2: Smart Contract Logic Errors (Examples: Poly Network, Nomad Bridge)
- How It Happened:
- Poly Network: A hacker found a vulnerability in the smart contract logic responsible for managing access rights to contract upgrade functions. They were able to change the addresses controlling the funds and withdraw assets.
- Nomad Bridge: The attack was caused by an error during a smart contract upgrade. A new Merkle root was initialized with a zero value, allowing any user to forge transactions and withdraw funds. The attack became "public," and many users began withdrawing funds by copying the initial exploiter's transaction.
- Lessons and How Mitosis Addresses This:
- The Problem: The complexity of bridge smart contracts inevitably leads to the risk of code errors that can be exploited.
- Mitosis Solution (Multi-Layered Approach):
- Security Audits: Thorough and multiple smart contract audits by independent, reputable firms are standard for Mitosis.
- Separation of Logic: Mitosis separates the message-passing logic (which can be handled by Hyperlane, also undergoing audits) from the liquidity management logic (EOL). This potentially reduces the complexity of each individual component.
- Formal Verification (Potentially): For critically important parts of contracts, formal verification might be applied, mathematically proving the absence of certain classes of vulnerabilities.
- Bug Bounty Programs: Incentivizing white-hat hackers to find and responsibly disclose vulnerabilities.
- Monitoring and Response: Systems for monitoring anomalous activity and rapid incident response plans (e.g., the ability for administrators or a DAO to temporarily halt the protocol if a critical vulnerability is detected).
Case 3: "Empty" Bridges and Asset Attractiveness (A common problem for many bridges)
- The Problem: Traditional bridges often operate on a "lock-and-mint" model (assets are locked on one chain, and their wrapped versions are issued on another). This creates huge pools of locked "original" assets, which become an extremely attractive target for hackers. If the bridge is hacked, these original assets can be stolen, and the wrapped tokens on the other chain lose their value.
- Lessons and How Mitosis Addresses This:
- The Problem: Large volumes of locked assets on the bridge side are a magnet for attacks.
- Mitosis Solution (Ecosystem-Owned Liquidity - EOL): The EOL model changes this dynamic. A significant portion of the liquidity used for cross-chain transfers is owned by the Mitosis protocol itself and strategically distributed across networks.
- Reduced Attractiveness of Attacking the "Vault": There isn't a single giant "vault" of user funds locked on the bridge side awaiting exchange. EOL liquidity is actively used and managed by the protocol.
- Focus on Message Passing Security: The main attack vector shifts from stealing locked assets to attempting to forge transfer messages. This is precisely the task addressed by the EigenLayer AVS integration, making message forgery economically unfeasible.
- Treasury Risk Management: The Mitosis Treasury, which manages EOL, has its own risk management, diversification, and monitoring protocols to protect the ecosystem-owned assets.
By studying these and other incidents, Mitosis aims to build a system where every potential attack vector identified in the past is met with a corresponding counter-mechanism. This is a continuous process of learning and adaptation, vital for survival and success in the aggressive Web3 environment.
3. Conclusions: Security as an Ongoing Process
Mitosis: A Proactive Approach to Security
Analyzing past cross-chain bridge hacks is not just an academic exercise for the Mitosis team. It is a fundamental part of the design and development process aimed at creating the most secure environment possible for user assets. Instead of reacting to threats retrospectively, Mitosis proactively embeds mechanisms into its architecture designed to prevent known attack vectors.
Key aspects of Mitosis's proactive security approach:
- Reliance on Economic Incentives, Not Trust: Using EigenLayer AVS shifts the security paradigm from trusting a small group of individuals to verifiable economic guarantees backed by ETH stakes. This significantly raises the bar for a successful attack.
- Defense in Depth: Mitosis's security does not rely on a single "silver bullet" mechanism. It is built from a combination of:
- A robust messaging protocol (e.g., Hyperlane with its configurable security modules).
- The cryptoeconomic security of EigenLayer AVS.
- Thorough smart contract audits.
- Bug bounty programs.
- Internal monitoring and incident response protocols.
- The unique EOL model, which changes the economics of potential attacks.
- Reducing Target Attractiveness: The EOL model, where the protocol owns and actively manages liquidity, differs from traditional bridges with huge static pools of locked user funds. This can reduce the motivation of attackers aiming for a "quick and large haul" from a single vault.
- Transparency and Openness (Prospectively): As the project develops, open-source code, public audits, and active community engagement on security matters will contribute to strengthening trust and identifying potential vulnerabilities.
Security is a Journey, Not a Destination
It is important to understand that in the world of cybersecurity, especially in the rapidly evolving Web3 space, there is no such thing as "absolute security." Threats constantly evolve, new attack vectors emerge, and even the most secure systems require constant attention and adaptation.
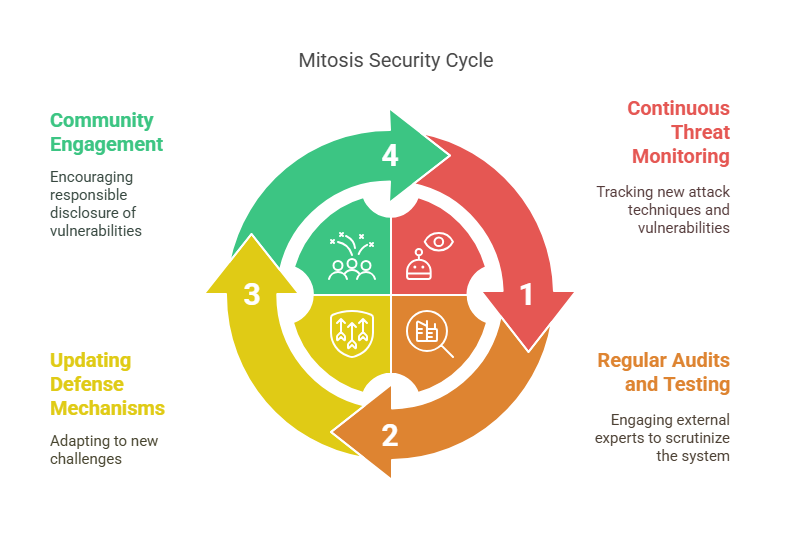
Therefore, Mitosis's approach to security is not a one-time action but an ongoing process that includes:
- Continuous threat monitoring: Tracking new attack techniques and vulnerabilities in related protocols.
- Regular audits and penetration testing: Engaging external experts to scrutinize the system.
- Updating and improving defense mechanisms: Adapting to new challenges.
- Community engagement: Encouraging responsible disclosure of vulnerabilities.
Conclusion: Choosing Mitosis, You Choose Deliberate Security
The history of cross-chain bridge hacks is full of tragic lessons. Mitosis demonstrates that these lessons can and should be learned. Instead of blindly copying outdated models, Mitosis offers an innovative approach where security is a cornerstone of the architecture.
The integration with EigenLayer AVS, the unique EOL model, multi-layered defense, and a proactive approach to risk management are all aimed at making interaction with Mitosis as safe as possible for users. Of course, no protocol is 100% immune to all possible threats, but Mitosis's commitment to learning from past mistakes and implementing cutting-edge security practices deserves attention.
When choosing a protocol for their cross-chain operations, users and developers must carefully evaluate its security model. Mitosis offers compelling arguments that it takes the protection of your assets seriously, building its "fortress" on a solid foundation of lessons learned and advanced technologies.
Learn more about Mitosis:
- Explore details on the official website: https://www.mitosis.org/
- Follow announcements on Twitter: https://twitter.com/MitosisOrg
- Participate in discussions on Discord: https://discord.com/invite/mitosis
- Read articles and updates on Medium: https://medium.com/mitosisorg
- Blog: https://blog.mitosis.org/


Comments ()