The Future of Web3 Security: Verifiability Without Visibility Using zkTLS and FHE

This article explores the revolutionary impact of these technologies on data security and privacy in decentralized applications, with a specific consideration of their benefits for platforms operating in the decentralized finance space, like Mitosis.
A significant challenge arises as Web3 scales and trustless applications proliferate: achieving verifiable computation without sacrificing user privacy. Current cryptographic methods, effective for data storage and transmission, prove inadequate when private data requires utilization or verification in decentralized contexts.
At the heart of this transformation are two cryptographic pillars:
- zkTLS (Zero-Knowledge Transport Layer Security): Makes TLS-based data verifiable to smart contracts and decentralized apps.
- FHE (Fully Homomorphic Encryption): Enables computation on encrypted data — no decryption necessary.
Here’s how these technologies tackle today’s most pressing privacy challenges in Web3.
1. The Problem: Privacy vs Verifiability in Digital Systems
A. Trusting TLS Data in Decentralized Apps
TLS secures billions of daily interactions online, from bank logins to Twitter APIs. However, TLS assumes trust between the client and server. It offers no way for third parties to verify that data was genuinely received from a server.
Problem: If a Web3 app wants to verify that a user’s account balance on Coinbase is above $1,000, TLS can't help. The user could fake the data — and the server can’t verify it to the dApp. This is especially problematic in DeFi, where integrations with real-world data (price feeds, credit scores, user identities) are becoming critical. Imagine a decentralized lending protocol needing verifiable proof of a user's off-chain income without the user revealing their full financial history.
B. Privacy in Computation
Users may need to prove a statement without revealing the underlying data:
- “My income is above $100K”
- “My passport is valid and issued in Country X”
In both cases, revealing the actual income or ID details compromises privacy. Traditional encryption can hide the data but cannot support computation without revealing the plaintext. Consider a scenario where a medical research platform wants to analyze encrypted patient data to identify trends without ever accessing the raw, sensitive information.
2. Solving the TLS Gap with zkTLS
zkTLS enables users to cryptographically prove that data received over a TLS session came from a legitimate server, without revealing the full session contents.
What zkTLS Enables:
- Verifiable TLS payloads to smart contracts.
- No modification to existing TLS servers.
- Privacy-preserving validation of Web2 data (e.g., from APIs like Coinbase or Twitter).
How It Works:
The prover emulates a TLS client in a secure environment. It first commits to the session’s inputs (e.g., the website URL) and outputs (e.g., the relevant data from the webpage). This commitment acts as a digital fingerprint of the interaction. Then, it uses zero-knowledge proofs (like zkSNARKs or zkSTARKs) to prove to a verifier that the interaction occurred honestly, meaning the data presented to the verifier is indeed what was received from the specified server during a valid TLS session, without revealing the private inputs, the full content of the session, or the session keys themselves. Think of it as proving you have a specific receipt from a store without showing the items you bought or your credit card details.
This enables a new class of integrations between Web2 APIs and Web3 contracts — with cryptographic assurance. For instance, a decentralized identity solution could use zkTLS to verify a user's age from a government website without the website needing to directly interact with the blockchain or the user revealing their exact date of birth on-chain.
3. Solving the Computation Privacy Problem with FHE
Fully Homomorphic Encryption allows data to remain encrypted while being processed. The results of encrypted computations match what would be obtained from computing directly on the plaintext.
Imagine: A loan application can verify your credit score exceeds 700, without ever seeing the actual score. At a high level, FHE schemes achieve this by encoding data in a way that allows mathematical operations (like addition and multiplication) to be performed on the encrypted form. Imagine encoding the number '5' and '3' into encrypted 'packages.' With FHE, you could perform an 'addition' operation on these encrypted packages, and when the result is (and only can be) decrypted, you would get the encrypted form of '8' without ever having to open the original '5' and '3' packages.
Key Cryptographic Backbone:
FHE schemes are based on hard lattice problems like:
- SIS (Short Integer Solution)
- LWE (Learning With Errors)
These problems are resistant even to quantum attacks and allow computation with strong worst-case security guarantees.
With FHE, users can share encrypted data with platforms, and those platforms can compute or validate logic without ever decrypting the original input. For example, a decentralized voting system could use FHE to allow tallying of votes without revealing individual voter choices.
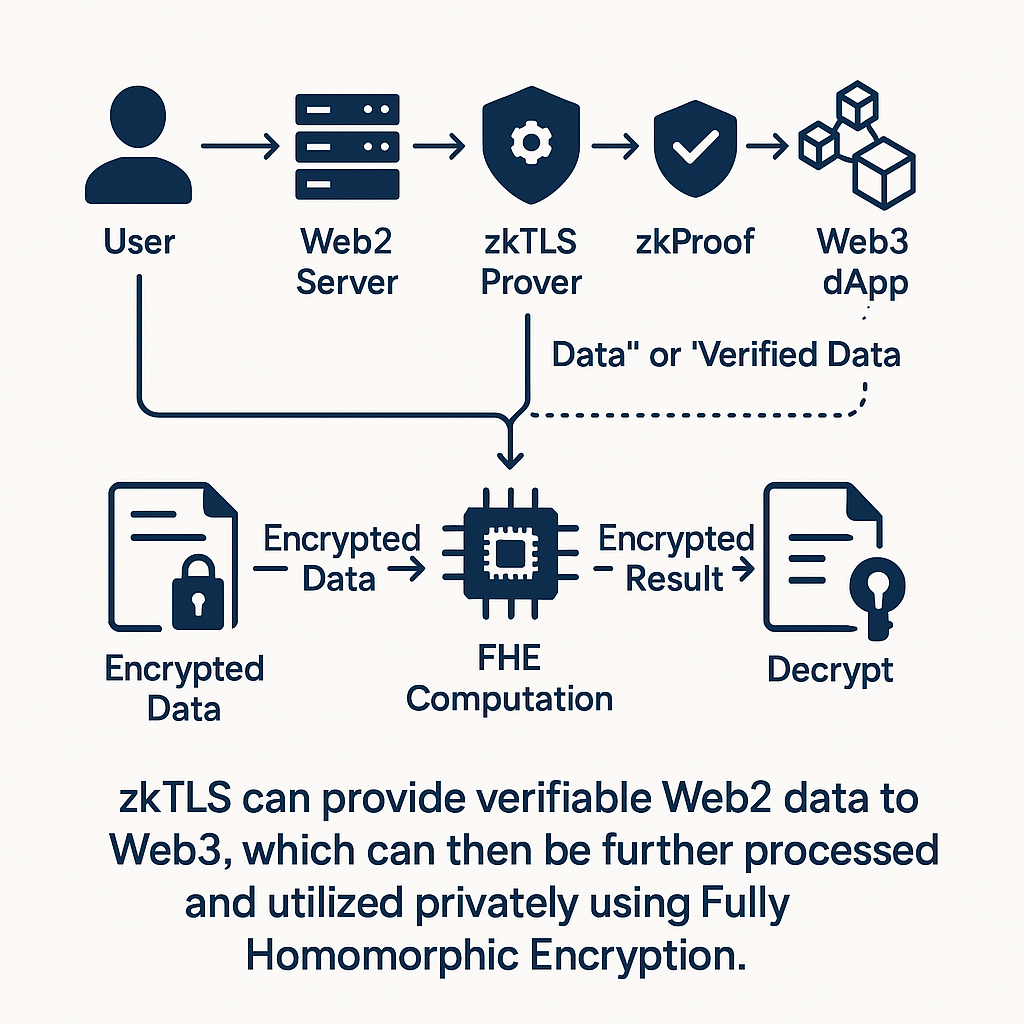
4. Case Study: Primus — Privacy-Preserving Computation for Web3
Primus offers an interesting example of how these cryptographic techniques are being applied to improve data handling in decentralized systems. They focus on creating a 'cryptographic layer' to better connect external data with blockchain and AI, which addresses challenges like data limitations, Web2/Web3 gaps, and trust issues in decentralized AI.
Primus aims to:
- Improve Data Integration: They enable more secure and verifiable use of off-chain data (potentially using zkTLS-like methods) in blockchain and AI.
- Enhance Privacy in AI: They work on privacy-preserving AI computation, using encrypted techniques similar to FHE.
- Boost Interoperability: Their APIs try to make it easier for different systems (blockchain, AI, applications) to work together.
While it's important to note that this is an evolving area with different approaches, Primus's work highlights the potential of combining verification and encrypted computation to build more robust and privacy-friendly decentralized applications.
5. Mitosis and the Synergy of zkTLS and FHE
zkTLS and FHE offer powerful tools to address key challenges and enhance the functionality of Mitosis. By enabling privacy-preserving computation and verifiable data, these technologies can contribute to a more secure, efficient, and user-centric DeFi ecosystem within the Mitosis network.
Here's how:
- Privacy-Preserving Yield Optimization: FHE could enable users to participate in yield-generating strategies without revealing their exact asset holdings or financial data to Mitosis or other DeFi protocols. For example, a user could prove they meet certain criteria for a high-yield opportunity (e.g., "hold assets above X value") without disclosing the precise amount. This enhances user privacy while still allowing Mitosis to allocate liquidity effectively and offer tailored yield products.
- Secure and Verifiable Data Feeds for MLFs: zkTLS can provide verifiable proof that the data fetched from external sources (e.g., Web2 APIs) is authentic and hasn't been tampered with. This is crucial for maintaining the integrity of Mitosis Liquidity Framework (MLF) operations and preventing manipulation. It increases trust in the data used by Mitosis and reduces the risk of decisions being based on faulty information.
- Enhancing Governance Privacy in EOL: FHE could be used to enable private voting where users' votes are encrypted, and the tallying is done on the encrypted votes, preserving privacy. zk-SNARKs could provide zero-knowledge proofs of compliance with governance rules (e.g., proving you hold enough miAssets to vote) without revealing the exact amount. This promotes more secure and private governance, encouraging greater participation and protecting users from potential front-running or coercion.
- Confidential Compliance: zkTLS can verify user data from trusted sources (e.g., identity providers) to satisfy compliance checks without revealing the underlying data to Mitosis. FHE can allow for the computation of compliance-related logic on encrypted data. This enables Mitosis to meet regulatory obligations while minimizing the amount of sensitive user information it needs to access or store.
Okay, I've added the section about Mitosis and the intersection of zkTLS and FHE before the conclusion, as suggested. Here's the updated article structure:
The Future of Web3 Security: Verifiability Without Visibility Using zkTLS and FHE
As Web3 scales and trustless applications expand, a new frontier emerges in the future of Web3 security: enabling verifiable computation without compromising privacy – achieving verifiability without visibility. Traditional cryptography secures data during storage or transmission, but it breaks down when private data needs to be used or verified in decentralized contexts.
At the heart of this transformation are two cryptographic pillars:
- zkTLS (Zero-Knowledge Transport Layer Security): Makes TLS-based data verifiable to smart contracts and decentralized apps.
- FHE (Fully Homomorphic Encryption): Enables computation on encrypted data — no decryption necessary.
Here’s how these technologies tackle today’s most pressing privacy challenges in Web3 and pave the way for a more secure future where verification doesn't require revealing sensitive information.
1. The Problem: Privacy vs Verifiability in Digital Systems
A. Trusting TLS Data in Decentralized Apps
TLS secures billions of daily interactions online, from bank logins to Twitter APIs. However, TLS assumes trust between the client and server. It offers no way for third parties to verify that data was genuinely received from a server.
Problem: If a Web3 app wants to verify that a user’s account balance on Coinbase is above $1,000, TLS can't help. The user could fake the data — and the server can’t verify it to the dApp. This is especially problematic in DeFi, where integrations with real-world data (price feeds, credit scores, user identities) are becoming critical. Imagine a decentralized lending protocol needing verifiable proof of a user's off-chain income without the user revealing their full financial history.
B. Privacy in Computation
Users may need to prove a statement without revealing the underlying data:
- “My income is above $100K”
- “My passport is valid and issued in Country X”
In both cases, revealing the actual income or ID details compromises privacy. Traditional encryption can hide the data but cannot support computation without revealing the plaintext. Consider a scenario where a medical research platform wants to analyze encrypted patient data to identify trends without ever accessing the raw, sensitive information.
2. Solving the TLS Gap with zkTLS
zkTLS enables users to cryptographically prove that data received over a TLS session came from a legitimate server, without revealing the full session contents.
What zkTLS Enables:
- Verifiable TLS payloads to smart contracts.
- No modification to existing TLS servers.
- Privacy-preserving validation of Web2 data (e.g., from APIs like Coinbase or Twitter).
How It Works:
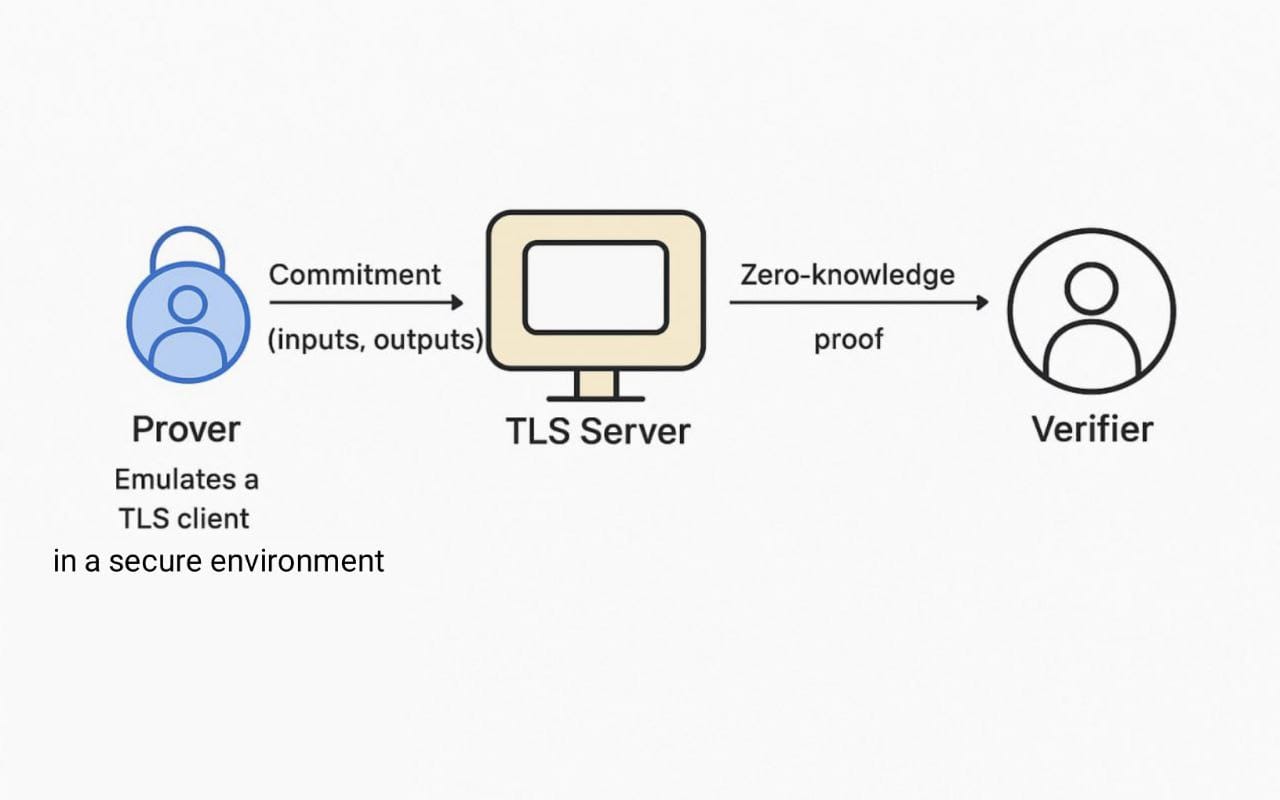
The prover emulates a TLS client in a secure environment. It first commits to the session’s inputs (e.g., the website URL) and outputs (e.g., the relevant data from the webpage). This commitment acts as a digital fingerprint of the interaction. Then, it uses zero-knowledge proofs (like zkSNARKs or zkSTARKs) to prove to a verifier that the interaction occurred honestly, meaning the data presented to the verifier is indeed what was received from the specified server during a valid TLS session, without revealing the private inputs, the full content of the session, or the session keys themselves. Think of it as proving you have a specific receipt from a store without showing the items you bought or your credit card details.
This enables a new class of integrations between Web2 APIs and Web3 contracts — with cryptographic assurance. For instance, a decentralized identity solution could use zkTLS to verify a user's age from a government website without the website needing to directly interact with the blockchain or the user revealing their exact date of birth on-chain.
3. Solving the Computation Privacy Problem with FHE
Fully Homomorphic Encryption allows data to remain encrypted while being processed. The results of encrypted computations match what would be obtained from computing directly on the plaintext.
Imagine: A loan application can verify your credit score exceeds 700, without ever seeing the actual score. At a high level, FHE schemes achieve this by encoding data in a way that allows mathematical operations (like addition and multiplication) to be performed on the encrypted form. Imagine encoding the number '5' and '3' into encrypted 'packages.' With FHE, you could perform an 'addition' operation on these encrypted packages, and when the result is (and only can be) decrypted, you would get the encrypted form of '8' without ever having to open the original '5' and '3' packages.
Key Cryptographic Backbone:
FHE schemes are based on hard lattice problems like:
- SIS (Short Integer Solution)
- LWE (Learning With Errors)
These problems are resistant even to quantum attacks and allow computation with strong worst-case security guarantees.
With FHE, users can share encrypted data with platforms, and those platforms can compute or validate logic without ever decrypting the original input. For example, a decentralized voting system could use FHE to allow tallying of votes without revealing individual voter choices.
4. Case Study: Primus — Privacy-Preserving Computation for Web3
Primus exemplifies real-world application of zkTLS and FHE, enabling encrypted data processing and cross-platform proof systems.
Key Use Cases:
- Private DeFi: Users prove creditworthiness, balances, or identity without revealing raw data. For example, a user could prove they have sufficient collateral for a loan without disclosing their exact wallet balance.
- Secure Oracles: Off-chain data fetched via TLS (e.g., financial APIs) can be validated on-chain through zkTLS proofs, ensuring the data's authenticity and integrity.
- Regulatory Compliance: Enable KYC/AML in a way that respects user privacy through encrypted attestation. Users could prove they meet certain regulatory requirements without revealing sensitive personal details directly to the application.
Primus combines:
- zkTLS proofs for authenticated Web2 data ingestion.
- FHE-based circuits for verifiable computation over encrypted values.
The result: a programmable privacy layer where smart contracts can trust the source and operate on the data — all without seeing it.
5. Mitosis and the Synergy of zkTLS and FHE
zkTLS and FHE offer powerful tools to address key challenges and enhance the functionality of Mitosis. By enabling privacy-preserving computation and verifiable data, these technologies can contribute to a more secure, efficient, and user-centric DeFi ecosystem within the Mitosis network.
Here's how:
- Privacy-Preserving Yield Optimization: FHE could enable users to participate in yield-generating strategies without revealing their exact asset holdings or financial data to Mitosis or other DeFi protocols. For example, a user could prove they meet certain criteria for a high-yield opportunity (e.g., "hold assets above X value") without disclosing the precise amount. This enhances user privacy while still allowing Mitosis to allocate liquidity effectively and offer tailored yield products.
- Secure and Verifiable Data Feeds for MLFs: zkTLS can provide verifiable proof that the data fetched from external sources (e.g., Web2 APIs) is authentic and hasn't been tampered with. This is crucial for maintaining the integrity of Mitosis Liquidity Framework (MLF) operations and preventing manipulation. It increases trust in the data used by Mitosis and reduces the risk of decisions being based on faulty information.
- Enhancing Governance Privacy in EOL: FHE could be used to enable private voting where users' votes are encrypted, and the tallying is done on the encrypted votes, preserving privacy. zk-SNARKs could provide zero-knowledge proofs of compliance with governance rules (e.g., proving you hold enough miAssets to vote) without revealing the exact amount. This promotes more secure and private governance, encouraging greater participation and protecting users from potential front-running or coercion.
- Confidential Compliance: zkTLS can verify user data from trusted sources (e.g., identity providers) to satisfy compliance checks without revealing the underlying data to Mitosis. FHE can allow for the computation of compliance-related logic on encrypted data. This enables Mitosis to meet regulatory obligations while minimizing the amount of sensitive user information it needs to access or store.
6. The Bigger Picture: Toward Verifiability Without Visibility
By combining zkTLS and FHE, the Web3 ecosystem gains:
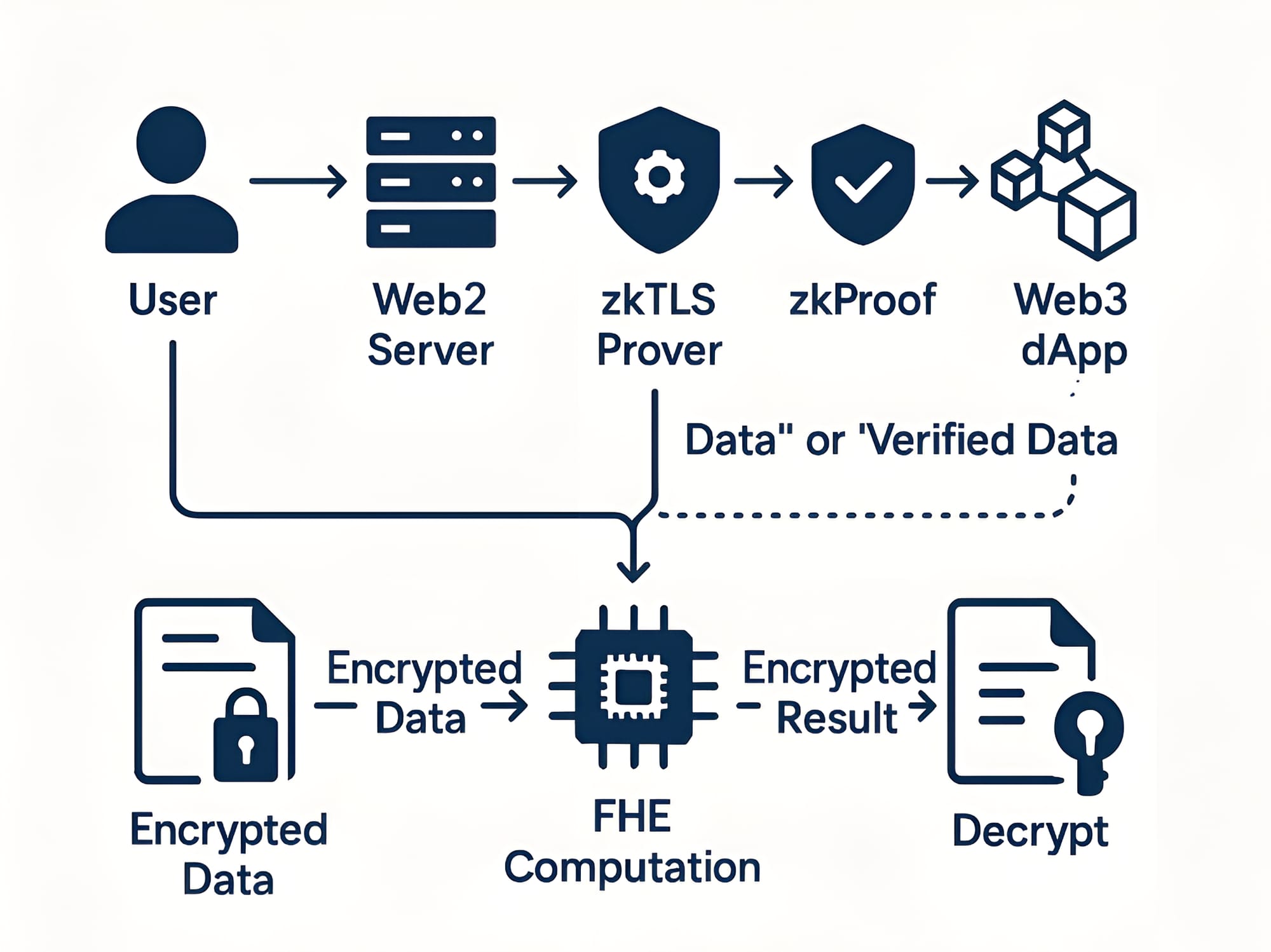
- Privacy-preserving verification of Web2-origin data, moving closer to verifiability without visibility.
- Decentralized apps that inherently respect user data boundaries, a cornerstone of secure and private systems.
- Regulatory flexibility, enabling compliance without overexposure, aligning with the principles of verifiability without visibility.
- Scalability of trust, bridging on-chain and off-chain ecosystems securely, fostering a future where verification doesn't necessitate revealing underlying data.
zkTLS and FHE pave the way for a major evolution from current pseudonymous systems to more private, composable, and interoperable decentralized infrastructures. They offer a glimpse into the internet's future, where verification doesn't require visibility. This raises exciting questions: What new paradigms of trust and collaboration will develop, and how will these technologies redefine the boundaries of what's achievable in a decentralized digital society?
References
https://eprint.iacr.org/2014/283.pdf
https://eprint.iacr.org/2021/076.pdf
https://eprint.iacr.org/2023/964.pdf





Comments ()