What Is Ransomware? Updated 2025 Threat Landscape, Protection Methods, and Real Examples

As cyber threats continue to evolve, ransomware remains one of the most significant and persistent risks in the world of cybersecurity. Since its first appearance in 1989, this type of malware has constantly advanced, now targeting not only individuals but also healthcare institutions, government agencies, airports, and critical infrastructure.
Definition of Ransomware
Ransomware is a type of malicious software that encrypts files on an infected device and demands a ransom for their release. It typically aims to create panic and force users to make payment within a limited time.
Modern ransomware uses advanced cryptographic algorithms to encrypt files in a way that is nearly impossible to reverse without the decryption key. Often, the ransom is requested in hard-to-trace cryptocurrencies.
As of 2025, ransomware spreads more rapidly and stealthily, utilizing AI-assisted targeting systems and automated network scanners to evade detection.
How Does Ransomware Spread?
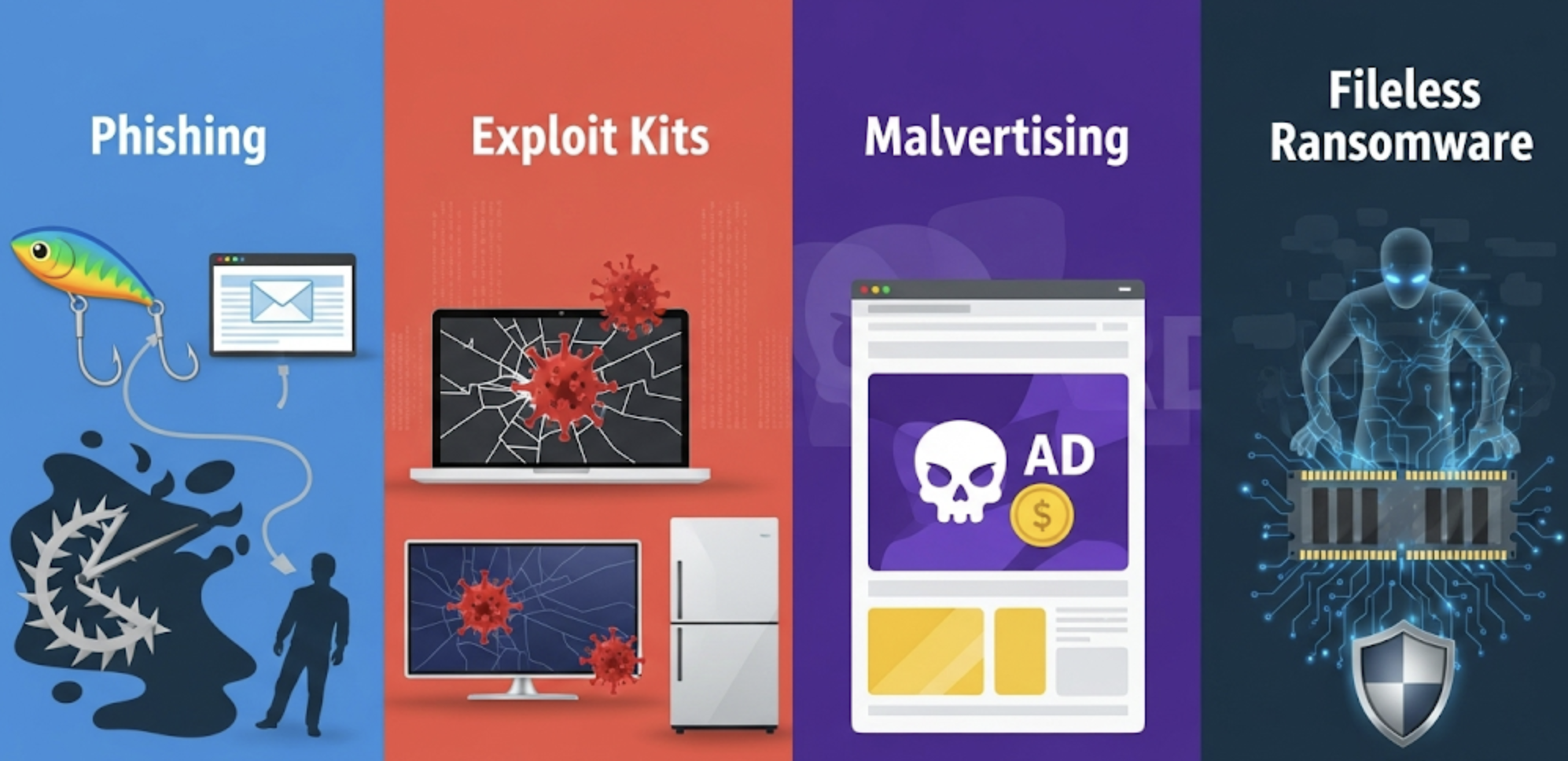
Ransomware distribution methods have diversified over the years. In 2025, attacks have become more sophisticated and harder to identify.
1. Phishing
Still the most common infection method. Victims are tricked via emails that appear to be from trusted sources. Clicking on a malicious attachment or link activates the malware.
2. Exploit Kits
These kits exploit vulnerabilities in outdated software to automatically install malware.
New Trend: Ransomware now targets IoT devices (such as smart TVs, security cameras, and smart refrigerators), looking for weak points in home and corporate networks.
3. Malvertising
Online advertising networks are used to spread malicious software. Infection can occur simply by clicking or even viewing the ad.
4. Fileless Ransomware
Emerging in 2025 as a major threat, fileless ransomware operates directly in system memory (RAM), leaving no traditional file trace and bypassing standard antivirus software.
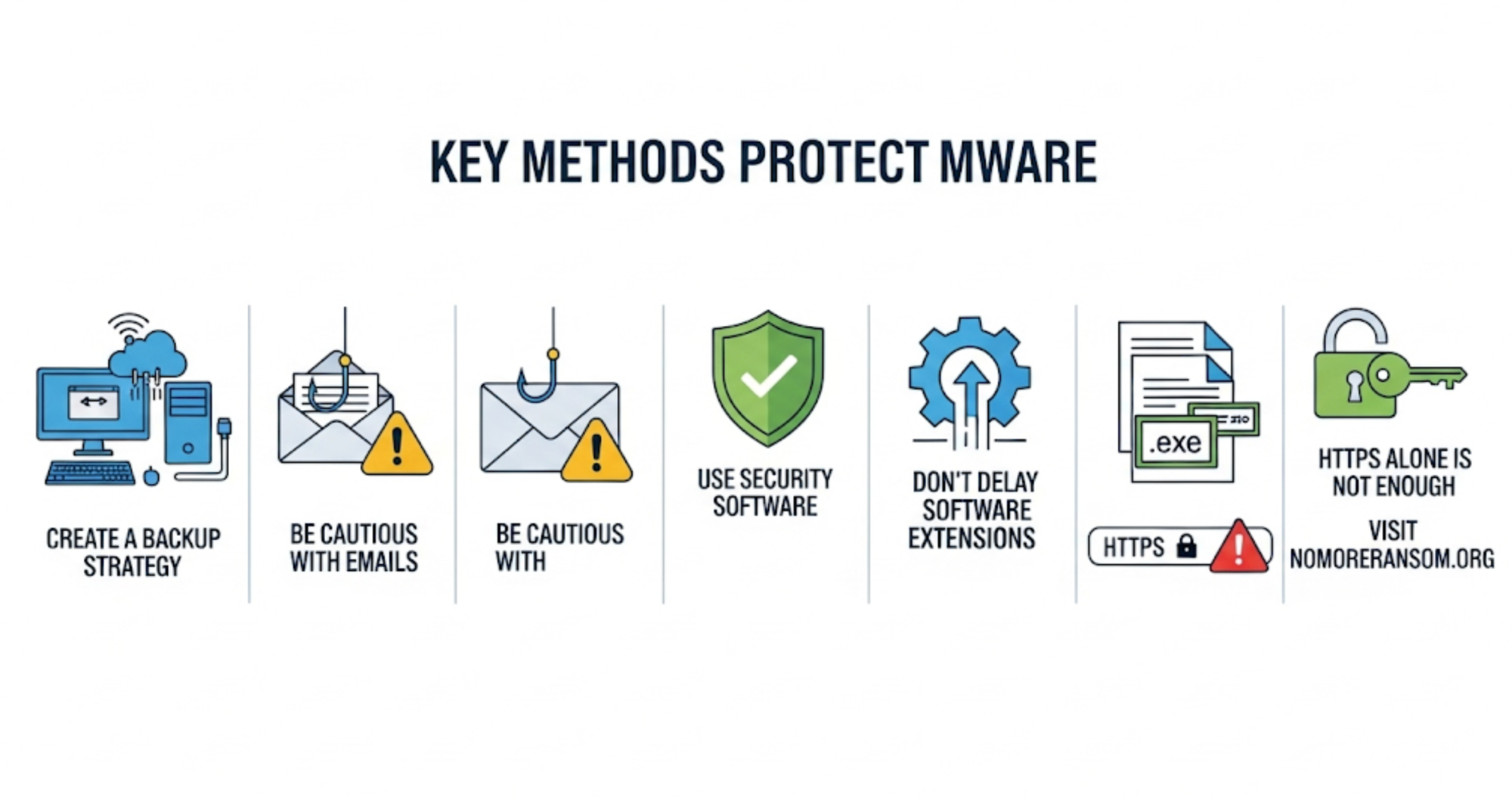
How to Protect Against Ransomware
1. Create a Backup Strategy
Back up your data regularly to external drives or secure cloud systems. Store critical backups offline where possible.
2. Be Cautious with Emails
Never open suspicious attachments especially those ending in .exe, .vbs, or .scr. Always question the sender and language used in the email.
3. Use Security Software
Install up-to-date and trusted antivirus software. Consider using dedicated anti-ransomware solutions for an extra layer of protection.
4. Don’t Delay Software Updates
Keep your operating systems, browsers, and applications updated. Patches fix vulnerabilities that ransomware may exploit.
5. Show File Extensions
Enable the "show file extensions" setting in Windows. This helps you identify potentially harmful file types disguised under misleading names.
6. HTTPS Alone Is Not Enough
Do not trust websites based solely on HTTPS. Many malicious sites now use HTTPS certificates to appear legitimate.
7. Visit NoMoreRansom.org
NoMoreRansom.org is a global initiative offering free decryption tools and prevention advice to ransomware victims.
Notable Ransomware Examples (Up to 2025)
GrandCrab (2018)
- Distribution: Malvertising and phishing emails
- Notable Feature: Demanded payment in DASH cryptocurrency
- Impact: Over 50,000 victims in a short time before being neutralized
WannaCry (2017)
- Spread Method: Exploited the EternalBlue vulnerability
- Impact: Over 300,000 devices in 150 countries
- Note: Microsoft released emergency patches to contain the outbreak
Bad Rabbit (2017)
- Distribution: Fake Adobe Flash updater
- Details: Required manual installation by users
- Primary Region: Mostly affected systems in Russia
Locky (2016)
- Infection Vector: Fake invoice emails
- Impact: Hollywood Presbyterian Medical Center paid 40 BTC in ransom
BlackBasta (2023–2024)
- Tactic: Double extortion (encryption + data leak threats)
- Target: Manufacturing firms in Europe
- New Feature: Negotiation and extortion via dark web portals
DarkVault (2025)
- Next-Gen Ransomware
- Uses AI to analyze corporate networks
- Automatically disables critical systems
- Stays hidden for 7 days to gather data before launching an attack
Conclusion: We Don’t Have to Live with Ransomware
Although ransomware has become more advanced alongside technological progress, it can largely be prevented with proper precautions. Both individuals and organizations can significantly reduce their exposure by raising awareness and using the right cybersecurity tools.
It’s essential to remember: ransomware is not only a technological issue it’s also a human factor problem. As such, user training and good cyber hygiene are just as critical as technical defenses



Comments ()